In 1967, computer security experts from Rand Corporation, Willis Ware, Rein Turn, Harold Petersen, and Benard Peters, worked on a report after a joint computer conference that declared communication mediums between computers were easily pierceable.
The first-ever penetration for breaching computer security was coined. And with it, James P. Anderson developed a step-by-step approach that formed the basis of penetration testing.
The structure was simple; security teams would move through several stages, from detecting a vulnerability to developing ways to counteract it. Here’s a brief history of penetration testing.
Exploiting a company’s security isn’t easy and requires skill and time. But with today’s technology, it’s easy for bad actors to find your organization’s vulnerable points. Penetrations target a company’s assets visible on the internet (for instance, a web application, the website, domain name servers (DNS), and emails) to gain access and draw out valuable data.
Using penetration tests, your enterprise can identify and fortify the possible surface of attacks before exploitation. Research backs it: A massive 73% of successful breaches have been through penetrating web applications from their vulnerabilities.
But more than ever, organizations need to validate the security of their applications, systems, and networks. Launching simulated tests is an effective way to ratify a system’s security strength and control measures. It’s not a one-time activity but a regular one. The frequency of the tests is based on your company’s organizational structure and risks unraveled from assessments.
Thankfully, penetration tests aren’t complicated. By equipping your IT teams with the necessary skills, your organization can consistently implement security, especially on significant infrastructure updates or the introduction of new digital services and assets.
And it all starts with understanding what the process is all about.
What is Penetration Testing?
Before diving into the how, it’d be best to answer the what and why. Penetration tests (often shortened as pen tests) are an officially accepted cyber-attack targeted at firms in a secure and controlled environment.
Blended within security audits, pen tests strive to uncover vulnerabilities under a managed scope of organization environment. Tactically, the tests take a similar approach to what a hacker follows. Some primary reasons why your enterprise needs pen tests include:
- Uncovering hidden vulnerabilities before attackers.
- Strengthening security processes and strategies.
- Lowering remediation costs and reducing dwell time.
- Adhering to regulatory compliance around security/privacy.
- Preserving your brand’s reputation and maintaining customer loyalty.
Pen tests screen your enterprise’s health (resilience to attacks) and demonstrate the ease at which hackers breach your systems. Additionally, insights gathered can be helpful in hierarchizing cybersecurity investments, following industry standards, and enhancing defensive strategies to safeguard your company from probable threats. But, it’s all possible through automated testing tools called penetration tools.
What are Pen Test Tools?
An ethical hacker uses pen test tools to evaluate the resilience of computing infrastructure through simulation of world attacks. By using these tools, security teams can eliminate repetitive testing work, generate test reports faster, and reduce the cost of multiple scanners.
As you might have guessed, there are numerous types: open source, web app, network, mobile app, cloud, manual, automated, and penetration testing as a service. Plenty as they are, it’d be best to look for key features like actionable reports, CI/CD integration, remediation support, and pen test certificates (only a few will offer publicly available pen test certificates).
With that foundation, let’s break down the penetration testing process.
Stages of Penetration Testing
In a typical penetration test, you will find several stages. While different resources will provide the process in different steps, the overall structure does not change. The process entails reconnaissance, scanning, assessing vulnerabilities, exploiting, and reporting.
Again, the best testers familiarize themselves with many tools to use the right tool at each testing phase. Each milestone of the process can be perceived as follows.
Information Gathering

Often left out, this phase helps your organization establish a common ground with the pen tester. At this stage, you’re defining the scope of work, engagement rules, timelines, and precise logistics with clear goals and objectives.
To have a complete and helpful pen test, this stage helps you understand the areas that need testing and the best methods. As a beginner step, you’d always be keen not to overlook it.
Before testing a system, an organization needs to consent to the tester. Otherwise, his actions can be considered illegal. Organizations lay out clear rules (in a contract) for a smooth workflow when engaging testers. The agreement should also depict critical assets, test goals, and precautions. Additionally, this step influences all subsequent actions. By the end, all plans are aligned with the expected test outcomes.
Reconnaissance/OSINT Gathering
In this phase, testers gather all available information about the system. The data acquired is tied to oncoming tests and driven by step one results. That way, testers get precise about the data to gather and strategies to implement. If you opt for an active reconnaissance, the tester directly engages systems. If you take the passive, publicly available information is obtained. For an extensive one, use both techniques.
Active data acquisition entails working with networks, operating systems, user accounts, domain names, mail servers, and applications. Passive data gathering is all about open-source intelligence; one could use social media, tax info, websites, and other public data.
Here are some open-source intelligence (OSINT) tools my colleagues and I have found useful and easy to use when collecting and relating information on the web. Using the OSINT framework, you can create an extensive checklist for entry points and vulnerabilities. While this step is key for internal and external pen tests, it’s not done in web applications, mobile apps, and API testing.
Scanning
An in-depth technical review of the system is next in line. Through scanning tools like automated vulnerability scanners and network mappers, you can understand how the target system reacts to various intrusions, open ports, network traffic, etc.
The main components of this stage are scanning and analyzing assets. You can use tools like Nmap to uncover computer services and hosts, send packets, and analyze responses. By the end of this stage, you’re equipped with information on assets. This includes operating systems, running services, and open ports.
By analyzing the results, you have the foundation to plot an exploit. You can map out the digital landscape of the system and locate possible points of attack. You can perform static and dynamic analysis to gain a clear understanding of the system’s response to different conditions.
Static analysis inspects the code of your applications while they are yet to be executed; you can use tools to scan code bases seamlessly. For the dynamic, you’re inspecting code as the application is running. Remember, the information gathered here needs to be accurate and obtained correctly, as the success of subsequent phases depends on it.
Assessment/Access Gain
At this point, all data gathered in the preceding steps helps pinpoint vulnerabilities and if they can be exploited. While this stage is helpful, it is super powerful when cascaded with other penetration test processes.
For evaluating the associated risks from discovered vulnerabilities, testers turn to multiple resources; one is the National Vulnerability Database (NVD), which analyzes software susceptibilities published in Common Vulnerabilities and Exposures (CVEs).
Next, you identify targets and map attack vectors. Target areas include high-value assets like employee data, customer info, partners/supply chains, vendors, ports, apps, and protocols. Web app attacks are launched.
The most common are SQL injection, cross-site scripting, and backdoors. The system is exploited by escalating privileges, traffic interception, and stealing data to reveal damage effects. Following the scope defined in the info-gathering stages, the tester is keen to work with the specified constraints.
Exploitation
Also known as the maintaining access stage, the tester checks whether the vulnerabilities can be used. This phase involves an actual breach and trial to access the system. By using tools like Metasploit, the tester simulates a real-world attack.
As this stage progresses, the tester is held accountable for an organization’s resources – ensuring that the systems aren’t compromised after simulations.
Metasploit is preferred for its smooth operations in exploiting vulnerabilities. This stage gauges the effects of a breach. The tester could try encrypting or exfiltrating data and simulate ransomware and zero-day attacks. The key to a successful pen test is striking a balance between pushing boundaries and maintaining a system’s integrity.
Experts are best to work with; they exploit vulnerabilities that slip through automation. By the end of this phase, you’ve tried to obtain high-level privileges in the system and network information by identifying the available data. The ethical hacker should also explain the results of exploits of high-value targets.
Risk Analysis and Recommendation, Review, Reporting

Moving past the exploitation phase, the tester generates a report documenting findings. The report should be used when fixing the uncovered vulnerabilities.
A good pen test report is a repository for well-documented vulnerabilities put into content that helps an organization remediate security risks. But the great one will be comprehensive about all discovered vulnerabilities and their CVVS scores, briefs of technical risks, possible impact on business, detailed coverage of exploitation difficulty, and tactical counsel.
Additionally, the reports should document all phases, test models, techniques used, and targeted assets. If possible, the tester will have an opinion on whether the test meets applicable framework needs. In conclusion, the report is best delivered with a general explanation and a technical guide.
After reporting and presenting reports, cleaning up the system is crucial. It is about reverting the system to how it was before the test restore modification to defaults. Clean-up activities entail withdrawing all executables, temporary files, and scripts from compromised systems, eliminating user accounts created to connect to the compromised system, and abolishing rootkits in the environment.
As the last of the steps, remediation falls into the hands of the organization. Guided by the penetration test reports and findings, the organization targets the vulnerabilities, analyzing potential impacts, informing decision-making to move forward, and influencing rectification strategies.
Since this stage is rounded by improving on past mistakes, remediating all exploitable vulnerabilities is constrained within a reasonable time. At times, this phase may extend for a while to have repeated tests on updates made or enact different tests.
Practical Application of Pen Tests: A Step-by-step Guide
For this example, we have chosen to use the Metasploit framework. You can create your custom workflow; here’s a typical one to get you going. Start by installing the framework.
If you’re on Linux/macOS, use the command:
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall && \
chmod 755 msfinstall && \
./msfinstallIf you’re on Windows, use the latest Windows installer. Or use the Shell command:
[CmdletBinding()]
Param(
$DownloadURL = "https://windows.metasploit.com/metasploitframework-latest.msi",
$DownloadLocation = "$env:APPDATA/Metasploit",
$InstallLocation = "C:\Tools",
$LogLocation = "$DownloadLocation/install.log"
)
If(! (Test-Path $DownloadLocation) ){
New-Item -Path $DownloadLocation -ItemType Directory
}
If(! (Test-Path $InstallLocation) ){
New-Item -Path $InstallLocation -ItemType Directory
}
$Installer = "$DownloadLocation/metasploit.msi"
Invoke-WebRequest -UseBasicParsing -Uri $DownloadURL -OutFile $Installer
& $Installer /q /log $LogLocation INSTALLLOCATION="$InstallLocation"And then…
Start a project – This will be your store for data and workspace. Since you may have different requirements for various subnets in your organization, organizing your work will improve your efficiency. For example, if you have a pen test for the IT and human resources teams, you’ll want to generate separate results.
Get Target Data – Here, you’re adding data to your project through a discovery scan or importing existing data. Scan targets to enumerate open ports to view a network’s services. Use the scan option. Next, enter the IP addresses you’d like to work on, each in a single line. You can also use the import option to import data from a local file.
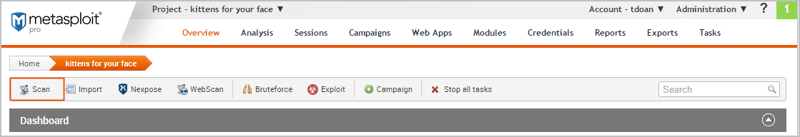
View/Manage Host Data – You can glance at the data from the host or project level. You can toggle through each IP to have a single host view.
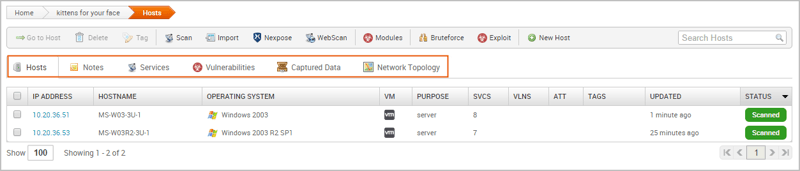
Scan for Vulnerabilities – Launch a vulnerability scan through the Nexpose options. This step leverages vulnerability databases to match if any is found.
Exploit Vulnerabilities – You can exploit vulnerabilities through a seamless validation wizard. Alternatively, the Nexpose will still work.
Post Exploit Activity – Collect data from the exploit through the session tab; click on “collect“.
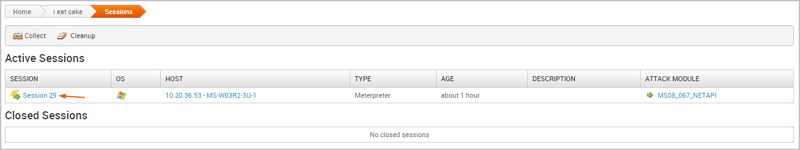
Clean Up – When done collecting data, use the “clean up” option to terminate the session and clear up the system.
Generate Reports – At the end of the pen test, Metasploit provides you with a number of reports that are a starting point for data consolidation and result compilation.
A detailed quick start guide on pen tests can be found on Metasploit’s Quick Start Guide.
Common Pen Test Tools
Some common tools include Sn1per, Metasploit, and Commix.
#1. Sn1per
Sn1per is a vulnerability investigation tool that validates the impact of client-side attacks in hack instances. You can use it to simulate remote and user-end attacks in a controlled environment. Sn1per has 6k GitHub stars. It also acts as the media outlet on the tool. With Sn1per, you can save time by automating open-source and commercial tools to enumerate vulnerabilities.
#2. Metasploit
Metasploit is a giant pen test framework developed by the unity of shared knowledge between open-source communities. It has 31.2k stars on GitHub, indicating a strong interest in the software world. Metasploit is backed by a collaboration of security enthusiasts envisioned to address vulnerabilities and enhance security awareness.
#3. Commix
Commix is a great OS command injection exploitation tool. While Commix specializes in command injection vulnerabilities, it’s easy to use, free and open-sourced, cross-platform compatible, portable, and modularized. It got 4k GitHub stars. It’s free and open source.
Final Words
Breaking down the penetration testing stages is essential for enterprises to enhance the resilience of their digital products with increased cyber-attacks. As cyber criminals bypass traditional security solutions, simulating real-world attacks through penetration testing is an effective way to navigate the ever-evolving cyber threat landscape.
By tailoring the pen test to your organization’s specific needs, you can ensure efficiency in security policies. Walking through all stages of the penetration test ensures you get the best ROI for your cyber security investments.
To have a successful pen test, be smart about it. Begin by acquiring information about the test. Build on that information to the reconnaissance level. A good starting point for your reconnaissance is defining the scope goals to be targeted on the system to be checked.
Next, scan the system to have an in-depth knowledge and identify vulnerabilities. Proceed to Launching an attack while keen not to damage the system. Then, generate helpful reports that guide remedy actions. Remember to clean up and restore the system to its original state.
When used correctly, penetration tests improve your organization’s security posture by identifying and fixing vulnerabilities. As many organizations migrate to the cloud and embrace new technologies, penetration tests are becoming critical to the information security domain. In fact, 75% of enterprises use pen tests to examine security posture. Or for compliance reasons. If you can give ample attention and treat each stage of the test independently, you’ll always find the value for running penetration tests.
Next, check out free online penetration testing (Pentest) tools to test application security.
Si quiere puede hacernos una donación por el trabajo que hacemos, lo apreciaremos mucho.
Direcciones de Billetera:
- BTC: 14xsuQRtT3Abek4zgDWZxJXs9VRdwxyPUS
- USDT: TQmV9FyrcpeaZMro3M1yeEHnNjv7xKZDNe
- BNB: 0x2fdb9034507b6d505d351a6f59d877040d0edb0f
- DOGE: D5SZesmFQGYVkE5trYYLF8hNPBgXgYcmrx
También puede seguirnos en nuestras Redes sociales para mantenerse al tanto de los últimos post de la web:
- Telegram
Disclaimer: En Cryptoshitcompra.com no nos hacemos responsables de ninguna inversión de ningún visitante, nosotros simplemente damos información sobre Tokens, juegos NFT y criptomonedas, no recomendamos inversiones



