The growing risks of cybersecurity attacks call for robust cloud data storage and deployment methods.
Cloud computing is a widely adopted concept that uses remote servers to provide on-demand access to computing resources, like applications, servers, and data storage. This flexibility of accessing resources from remote locations has significantly increased the adoption of cloud services.
According to the statistics, the cloud applications market is anticipated to grow from $100 billion in 2018 to a whopping $168.6 in 2025.
However, the increased cloud deployment has also increased the frequency of cloud security attacks. 45% of data breaches are cloud-based—making cloud security a significant concern for businesses of all types and sizes.
Hence, the need for new and modern security strategies has given birth to Cloud Native Security. It refers to the security measures to protect cloud-based data, applications, and infrastructure.
This blog will dive deeper into understanding Cloud Native Security—what it means, key concepts, best practices, vulnerabilities, and more. So, read along if you want to learn more about this concept!
What Is Cloud Native Security?
Cloud Native Security is a security practice of securing cloud-based applications, platforms, and infrastructure using a cloud computing delivery model.
Its primary focus is taking advantage of cloud computing’s unique characteristics, like scalability, automation, and agility.
It builds security from the beginning of the development process via production, ensuring multiple security layers and consistent monitoring to detect new vulnerabilities.
The modern Cloud Native architecture uses cutting-edge infrastructure and software technology to allow companies and enterprises to deploy their applications simultaneously and securely, emphasizing the cloud-first infrastructure.
How Does Cloud Native Security Work?
Cloud Native refers to reinventing, innovating, and transforming how companies perform software development.
While shifting security to the left of software development is gaining popularity, having security at every checkpoint and integrating security throughout the Software Development Life Cycle (SDLC) is much more efficient.
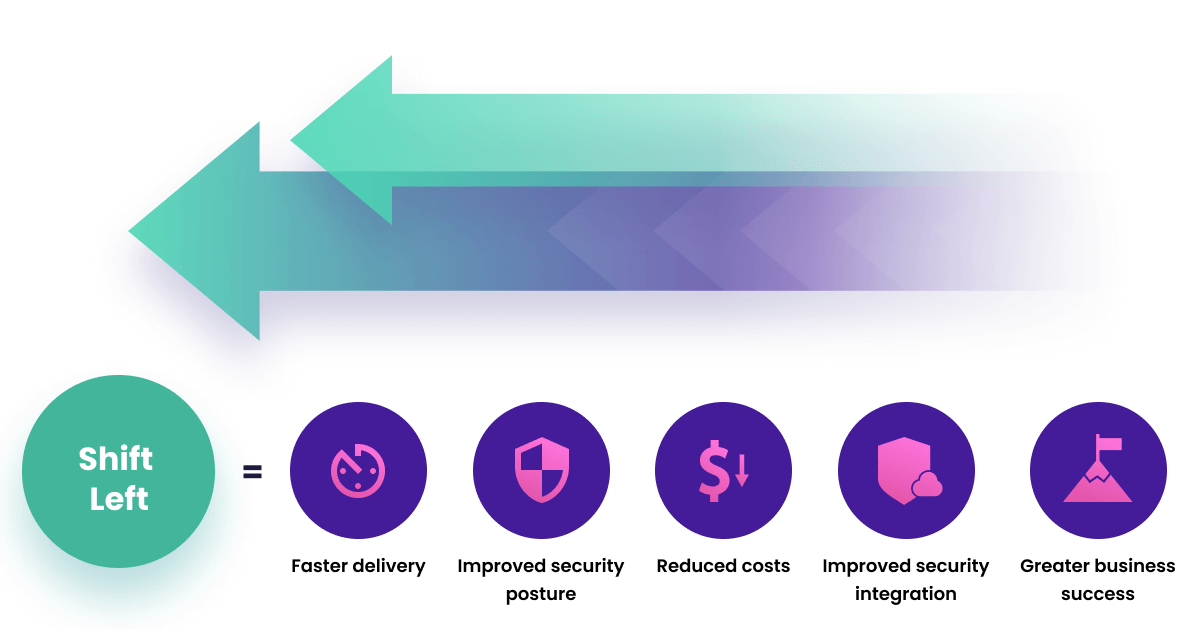
This shift-left method prioritizes security at the earliest SDLC stage—making it easier to fix vulnerabilities and prevent bottlenecks.
Cloud Native Security implements the same principle and addresses security concerns by fixing vulnerabilities correctly.
Here are a few efficient ways that Cloud Native Security works:
- Automated Deployment of Security Controls: Cloud Native Security uses automation to deploy security controls, like encryption and intrusion detection systems, to ensure updated and correct configuration of the security controls.
- Continuous Integration/Continuous Deployment (CI/CD): CI/CD pipelines enable fast and automated deployment of security patches and updates.
- Containerization: Cloud Native Security leverages containerization to secure and isolate data and applications.
- Microservices Architecture: Cloud Native Security uses a microservices architecture to reduce the impact of security concerns. If a security problem occurs in a microservice, it doesn’t always impact the entire application.
- Compliance: Cloud Native Security meets the regulatory standards and security certifications, like SOC 2 and ISO 27001, making organizations compliant with these standards.
Cloud computing scalability and agility allow organizations to respond quickly and address the changing security needs and demands—making Cloud Native Security a flexible and efficient solution for cloud data and applications security.
Importance and Goals of Cloud Native Security
Cloud Native Security aims to enable a robust security framework to ensure the utmost data and applications security and minimize the risks of cybersecurity threats.
Here are the key benefits of Cloud Native Security:
#1. Improved Monitoring and Visibility
Cloud Native Security enables continuous testing throughout all the CI/CD layers, enabling security teams to track and address security issues at the system and component levels.
Thanks to Cloud Native applications, you can easily monitor the utilization and usage logs. Ensuring the staff and other team members have minimum access to the resources and tracking the usage statistics by creating dashboards, understanding the usage pattern becomes much easier.
Thus, it rejects unauthorized user access attempts and sends alerts to signal such attempts.
#2. Ease of Management
Automation is one of the primary differences between traditional and Cloud Native Security or applications.
Cloud Native Security makes resources automatically available, with the capabilities for automatic problem-solving, auto-scalability, and automatic remedial action—making management a breeze.
It guarantees better management and a straightforward user experience for the team members.
#3. Enhanced Customer Experience

In Cloud Native technology, application updates are sent and distributed in tiny batches as part of a testing process.
It automatically gathers user feedback and suggestions simultaneously to make the required changes.
This process diminishes the concern about post-deployment and debugging, allowing developers to focus more on the characteristics of applications and customers’ responses to them.
#4. Automatic Threat Detection

The Cloud Native Security technology streamlines workflows and automatically identifies and removes threats by incorporating Machine Learning (ML) techniques and algorithms.
Its automated tools use past breach data mining and dynamic analysis tools to identify cybersecurity threats and notify the appropriate teams in advance.
It secures and remediates the applications in real time with the help of event-driven mechanization in case of data breaches.
#5. Continuous Compliance Assurance
Cloud Native applications enable compatibility with rules and regulations relevant to the cloud infrastructure’s use. For instance, localization legislation and data sovereignty regulations are responsible for protecting data.
While these laws and regulations differ with different domains and countries, a cloud infrastructure ensures compliance with these regulations by default—setting a standard for cloud security measures.
#6. Seamless Deployment and Flexibility
Cloud Native Security and applications demand rapid deployments—making it easier for security teams to apply security fixes across multiple environments.
This is important because outdated software and applications may have critical security implications; hence, updating the cloud infrastructure with the latest security measures is essential to prevent and combat evolving cybersecurity threats.
#7. Reduced Development Cost

All the Cloud Native Technology applications use microservices, which you can easily migrate between multiple projects.
Hence, whenever you need to make new applications, you must apply the old project’s microservices to the new one.
This process significantly reduces the development cost and allows developers to invest more time in the applications instead of the framework, as Cloud Native technology divides the framework into multiple services.
#8. Data Security
Cloud Native security uses powerful key-based data encryption algorithms to prevent external users and malicious hackers from accessing and intercepting data files and data that travel to and from the cloud.
Moreover, you can restrict access to sensitive data to authorized users only—because of this, organizations like banks move their data to the cloud.
#9. Network Security

Cloud Native deployments enable enhanced network security—thanks to security measures like ongoing network traffic surveillance for reporting and customizable firewall rules.
It also logs user access to and from the applications and the network traffic in the review applications.
This logging process of the application’s traffic flow develops a deep understanding of the application’s usage—making analyzing, detecting, and predicting network threats a breeze.
Thus, whether you want to manage vulnerabilities with ease and automate threat detection or enable high data security at an affordable cost, Cloud Native Security is a reliable option for your organization’s cloud infrastructure.
4 C’s of Cloud Native Security
Cloud Native Security follows a layered security approach, considered the best design for securing software and application systems.
A typical Cloud Native infrastructure consists of four security layers: Cloud, Code, Container, and Cluster.
Let’s look at each one of them and their significance.
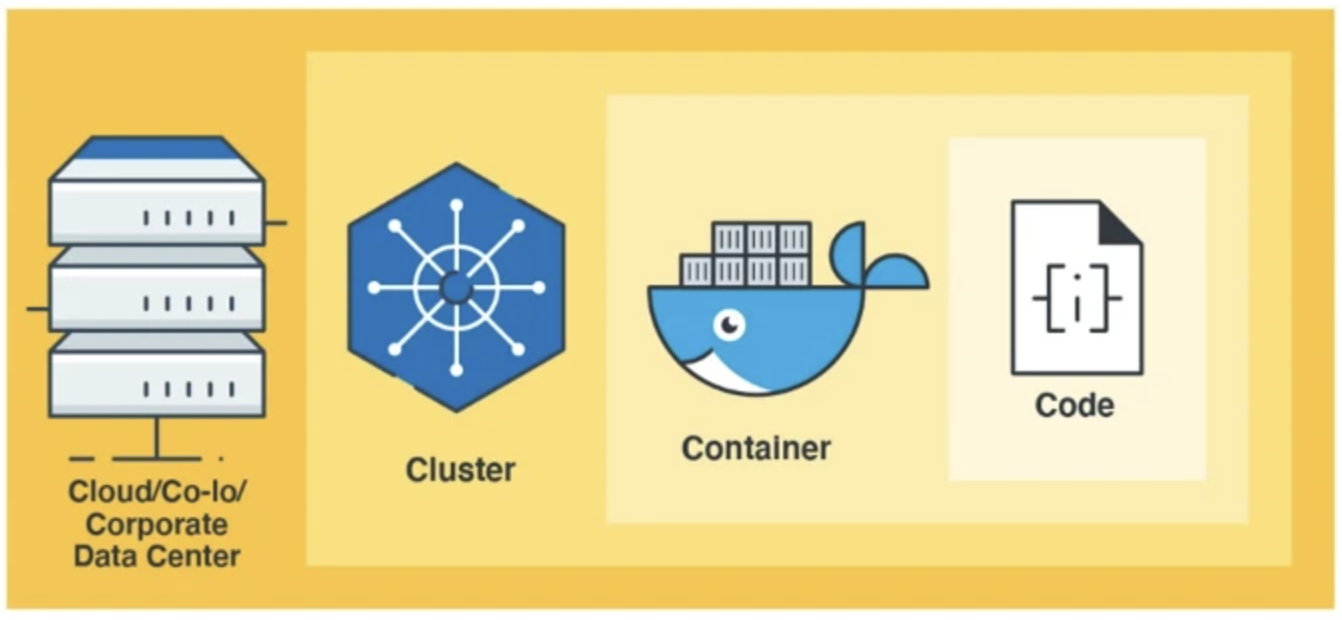
Cloud
The cloud infrastructure is the foundation of all the security layers and the base of configuring security for the applications.
Enabling application security at the cloud level is essential, as it’s difficult for developers to configure it at the code level. The cloud providers make distinct recommendations to run secure application workloads.
The cloud layer interface interacts with the external environments, including third-party plugins, users, and external APIs. Thus, security vulnerabilities in the cloud layer would significantly impact all the applications, services, and processes hosted within the cloud.
Cluster
After the cloud layer is the cluster layer, applications deployed within the cloud infrastructure are modularized into containers and grouped into different containers.
Protecting a cluster includes securing the software and applications running within the clusters and the secure communication configuration in the cluster.
Container
The container layer that comes after the code layer is the most crucial part of application and software deployment in Cloud Native Security deployments.
Since the software and environment are packaged into containers, protecting containers is unavoidable within modern cloud environments.
Code
The last ‘C’ is the code layer. Strengthening and developing cloud security through an application’s code is one of DevSecOps’s best practices.
It involves moving security down the application code level and prioritizing application security earlier in the software and application development lifecycle. Identifying security vulnerabilities earlier in the development lifecycle allows companies to save a lot of time, cost, and effort.
Cloud Native Security Vulnerabilities
While Cloud Native Security aims to modernize the cloud infrastructure and enterprise software architecture, it has security implications —which might surprise many.
Here are the common Cloud Native Security vulnerabilities you need to consider before integrating them within your infrastructure.
#1. Misconfigured Containers
Recently, NSA announced that misconfigurations are a common cloud vulnerability and threat.
Within the serverless Cloud Native world, it’s easy to spin up new web servers and create new containers. But without granular security, permissive network access is possible—leaving the cloud network for anyone to access.
Often, application developers make configuration changes or write configuration rules and policies applicable to the entire suite of applications. As a result, misconfigurations in the DevSecOps process could expose the data storage or create vulnerable workloads.
#2. Insecure Defaults
Not every Cloud Native tool and application is secure by default, as some come with flexible settings and configurations. However, according to Accurics’s study, 48% of Cloud Native applications’ security violations are because of insecure defaults.
Insecure defaults arise when the security teams deploy cloud-based systems with misconfigured or insufficient security settings, leading to compromised or leaked sensitive data.
Hence, it’s important to configure carefully and evaluable the cloud-based system’s security settings to prevent unauthorized access to sensitive information.
#3. Leaky Secrets
Storing sensitive information, like the encryption keys and database credentials within an application or the organization’s databases, can expose them to threats and security vulnerabilities.
In 2021, around 6 million passwords and sensitive information like API keys were stolen. Stolen credentials in bulk from a company’s database can put customers and end users at risk—leading to huge penalties.
Leaked secrets and data can lead to severe consequences like theft, service disruption, and unauthorized system access. Hence, it’s essential to properly secure and manage sensitive data through encryption, secure storage systems, and access controls, like Multi-Factor Authentication (MFA), to prevent the risk of over-permissiveness.
#4. Software Supply Chain Vulnerabilities
Just like there’s a supply chain for traditional products, there’s one for software products.
Many distribution models and third-party frameworks make designing and delivering the code to the production team possible. However, the risk of using third-party and cloud-based applications gives rise to software supply chain vulnerabilities.
This occurs when the software supply chain’s components, like the library or package, get compromised. In 2021, the software supply chain vulnerabilities, including open-source vulnerabilities, almost tripled.
A vigilant and proactive approach to Cloud Native Security, following the best practices, is crucial to reduce security risks.
Learning Resources
Here’s a list of helpful learning resources and books from Amazon to gain in-depth insight into Cloud Native Security and tips for integrating it within your systems.
#1. Cloud Native Security Cookbook: Recipes for a Secure Cloud (1st Edition)
Published in 2022, this Cloud Native Security Cookbook by Josh Armitage provides insight into how you can use Azure, AWS, and GCP to enhance your Cloud Native System’s security.
The author shares his experience on the trade-offs developers and security professionals need to make with different cloud providers and how they can implement the existing solutions to design more robust solutions.
#2. Cloud Native Security (1st Edition)
This comprehensive guide to Cloud Native Security by Chris Binnie covers a detailed study into minimizing the attack surface and mitigating cybersecurity risks to protect the Cloud Native infrastructure.
This is the best book if you want detailed knowledge about strengthening and hardening your Cloud Native estate.
#3. Kubernetes Security and Observability: A Holistic Approach to Securing Containers and Cloud Native Applications (1st Edition)
This book by Brendan Creane and Amit Gupta focuses on the key observability and security practices, allowing you to unleash the power of Cloud Native applications.
So, if you want to learn the architect of Kubernetes security for hybrid and multi-cloud environments, make sure you get your hands on this holistic guide.
#4. Practical Cloud Native Security with Falco: Risk and Threat Detection for Containers, Kubernetes, and Cloud (1st Edition)
This guide by Loris Degioanni introduces the readers to the concept of Falco, an open-source standard for continuous threat and risk detection across Kubernetes, cloud, and containers.
You can learn everything about Falco, from its deployment to writing your own security rules to speed up threat detection on your cloud infrastructure.
#5. Native Cloud Security A Complete Guide – 2019 Edition
If you need answers to your unique questions about Cloud Native Security, this book is for you.
The author Gerardus Blokdyk provides all the essential tools you require for an in-depth Cloud Native Security Self-Assessment, allowing you to identify areas of improvement within your Cloud Native Security Infrastructure.
Conclusion: Cloud Native Security is the Future
Gartner predicts that over half the spending of IT companies will be shifted from the traditional IT infrastructure to the public cloud by 2025—a jump from 41% in 2022.
However, of all the benefits these IT companies gain from cloud infrastructure, security remains one of the major challenges they face—mainly because of employee faults, misconfigurations, and inherent architectural vulnerabilities.
So, ensure you understand the importance, goals, benefits, and best practices of Cloud Native Security through this blog and the learning resources mentioned to enable a scalable and agile Cloud Native application infrastructure for your organization.
Next, check out the best vulnerability management software.
Si quiere puede hacernos una donación por el trabajo que hacemos, lo apreciaremos mucho.
Direcciones de Billetera:
- BTC: 14xsuQRtT3Abek4zgDWZxJXs9VRdwxyPUS
- USDT: TQmV9FyrcpeaZMro3M1yeEHnNjv7xKZDNe
- BNB: 0x2fdb9034507b6d505d351a6f59d877040d0edb0f
- DOGE: D5SZesmFQGYVkE5trYYLF8hNPBgXgYcmrx
También puede seguirnos en nuestras Redes sociales para mantenerse al tanto de los últimos post de la web:
- Telegram
Disclaimer: En Cryptoshitcompra.com no nos hacemos responsables de ninguna inversión de ningún visitante, nosotros simplemente damos información sobre Tokens, juegos NFT y criptomonedas, no recomendamos inversiones


