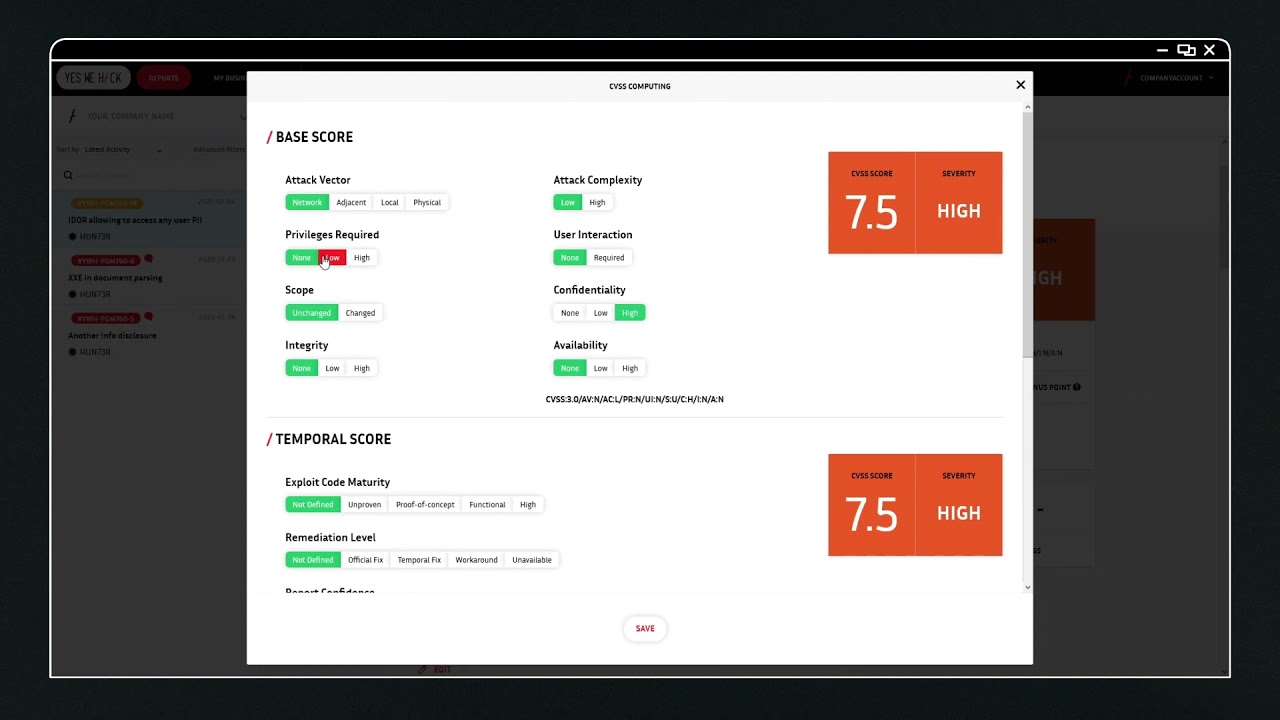
Security vulnerabilities can manage to get through robust security walls and exploit software and applications with evolving sophisticated cybersecurity threats.
No matter what defensive security tools you might use to defend your organization, preventing bugs altogether and staying entirely out of the reach of hackers is a far-fetched dream in today’s digital world.
The only way to minimize the risks of cyberattacks and prevent the repercussions of software bugs is to identify and remove them at the earliest. This is why organizations have been increasingly relying upon and seeking bug bounty hunters to address and remove malicious bugs and vulnerabilities—before they cause major damage.
The bug bounty program is gaining immense popularity, and big tech companies are leveraging this program to address cybersecurity risks. For instance, Meta received 10,000 bug reports by paying $2 million in bounties. Moreover, the average spend on bug bounties grew from $2000 in 2021 to $3000 in 2022, while the average payout grew to a whopping $26,728 from $6443 in 2021.
So, if you want to leverage the lucrative nature of bug bounty programs and become a bug bounty hunter to help organizations stay secure—you’re on the right page.
In this article, we’ll walk you through what bug bounty is, its benefits, what skills you require to become a bug bounty hunter, how to become one and stay updated, and more.
Let’s begin!
Understanding Bug Bounty Hunting
A bug bounty, penetration testing, or ethical hacking is a monetary reward given to white-hat hackers for successfully identifying and reporting security bugs and vulnerabilities in any software or application.
Bug bounty hunting is hunting or looking for bugs or technical errors in the coding scripts of website programs, applications, or software that can potentially compromise their security.
Several big tech companies and global organizations employ bug bounty programs and initiatives and hire skilled and talented bug bounty hunters who can efficiently spot vulnerabilities to secure their software or website environment and, in return, reward the bounty hunters for their skills.
Let’s understand the role of a bug bounty hunter in more detail.
Who Is a Bug Bounty Hunter?

Cybercriminals are always looking for software bugs and vulnerabilities to penetrate through them and compromise the application or the software.
Once in, these bugs can lead to data breaches and other cyberattacks—leading to major reputational and financial losses—which are sometimes beyond repair.
In such cases, bug bounty hunters help organizations find security loopholes and weak, vulnerable spots to immediately fix them and make organizations resistant to any form of cyberattacks.
Thus, bug bounty hunters act as security experts and professionals who help businesses hunt bugs in their digital assets and report them on time—to enable early risk mitigation.
Advantages of Bug Bounty for Organizations and White-Hat Hackers
A bug bounty program benefits both organizations and bounty hunters, who are nothing but ethical or white-hat hackers.
Here’s how a bug bounty program benefits any business or organization:
- Improved overall security by reducing risks of security vulnerabilities, data breaches, and other cybersecurity attacks.
- Cost-efficient, enabling organizations to identify and address vulnerabilities before cybercriminals could exploit them—saving organizations from costly breaches and legal liabilities.
- Enhanced the organization’s reputation and trustworthiness amongst consumers—boosting customer trust and demonstrating a commitment to security.
- Enabling organizations to meet regulatory and compliance requirements for vulnerability disclosure and security testing.
Here are the benefits of a bug bounty program for a bounty hunter:
- Enables ethical hackers to leverage financial rewards and earn money through their skills and talent.
- Gain public acknowledgment and recognition with badges and certifications from the organizations—enhancing professional visibility and credibility.
- Develop and hone the hacker’s skills in cybersecurity, ethical hacking, and penetration testing—allowing them to gain real-world vulnerabilities knowledge and experience.
Bug Bounty Hunter Prerequisites: Essential Skills Required
Organizations pay or reward bug bounty hunters based on the detected bugs, the program’s scope, the bug’s severity, and other factors.
However, to get paid handsomely before even enrolling in a bug bounty program, knowing the prerequisites of a bug hunter and acquiring all the essential skills is a must.

Here are the fundamental skills you must acquire if you wish to become a successful bug bounty hunter:
#1. OWASP Top 10
OWASP Top 10 is a documentation for ethical hackers and developers that comprises the 10 most critical web application security risks and ways to mitigate them.
It’s great documentation for aspiring bug bounty hunters to find and mitigate risks like broken access control, injection, insecure design, cryptographic failure, security misconfiguration, identification and authentication failure, and more.
#2. Knowledge of Web Technologies
A solid understanding and knowledge of web technologies, like HTML, Javascript, and CSS, is critical to becoming a bug bounty hunter and finding security vulnerabilities within software and web applications.
Moreover, having basic backend knowledge and learning PHP, ASP.NET, and Java can help you stand out as a bug bounty hunter.
#3. Computer Fundamentals and Networking (TCP/IP)
A basic prerequisite for a bug hunter is learning computer fundamentals, including input-output systems, data, components, processing, and information.
In addition, studying TCP and IP protocols, forming IP addresses, and OSI layers is also crucial when becoming a bug bounty hunter.
#4. Internet (HTTP)
Understanding the workings of the HTTP protocol, how the internet works, how websites are connected to the internet and make connections, and how users visit websites online is also essential to help identify and mitigate online bugs and server vulnerabilities as a bug bounty hunter.
#5. Knowing Common Programming Languages
While learning programming languages isn’t mandatory for a bug bounty hunter, knowing languages like Python, Perl, Ruby, etc., can help you read a developer’s mind and find vulnerabilities much quicker and easily.
#6. Operating Systems
Understanding the Linux operating system, especially Kali Linux, is critical as it provides many pre-installed tools for pen-testing, hacking, and bug hunting.
#7. Command Line Interface
A bug bounty hunter must have basic knowledge and good enough hands-on practice with the Microsoft Windows OS’s terminal and the command line interface.
It can help you have basic knowledge of things like directly connecting the kernel with the system.
Websites and Forums to Stay Updated as a Bug Bounty Hunter
As cyberattacks become more sophisticated each day, staying up-to-date and informed with the latest cybersecurity threats, vulnerabilities, and techniques is essential as a bug bounty hunter.
While several websites, resources, and forums are available, too much information can easily confuse you, especially as a beginner.
Here are a few critical forums, websites, and channels you can refer to stay up-to-date as a bug bounty hunter:
- Bug bounty community platforms: HackerOne, Synack, and Bugcrowd are some of the best and most credible bug bounty platforms that regularly share and post updates, tips, and success stories of bug bounty hunting on their dedicated blogs, newsletters, and forums.
- Bug bounty forums: Participating in the bug bounty forums, like Bugtraq and 0x00sec, and Reddit forums, like Reddit/r/netsec, also act as a great source of free, credible knowledge and facilitate discussions amongst bounty hunters.
- Security blogs and news: Another great tip is to follow cybersecurity blogs and news websites, including KrebsOnSecurity, Threatpost, Troy Hunt’s Blog, The Hacker News, and InfoSec Institute.
- Webinars and conferences: Attending in-person or virtual webinars and conferences, like the RSA Conference, DEF CON, and Black Hat, which often feature talks about bug bounty hunting, is a great way to stay updated about the latest bug bounty news and trends.
- Bug bounty Discord servers: Several bug bounty communities Discord servers are available that allow its members to chat, collaborate in real-time, and share information and news to stay informed about the different bug bounty programs or news.
- LinkedIn groups: You can also join cybersecurity and bug bounty hunting-related LinkedIn groups to stay at [par with the latest news and network with cybersecurity professionals.
- Podcasts: Security podcasts, like Darknet Diaries and Security Now!, are one of the most efficient and convenient ways to stay updated about the current cybersecurity trends and success stories.
- Online courses and training programs: You can also enhance your skills and learn about bug bounty hunting trends by enrolling in online courses on platforms like edX, Coursera, Udemy, and more.
Next, we will explore how to enroll in bug bounty programs.
How to Enroll In Bug Bounty Programs?
Once you’ve learned all the skills and prerequisites of bug bounty and the forums to stay updated, let’s learn the next steps you must take as a bug bounty hunter.
Here is the step-by-step guide to enrolling in a bug bounty program, contributing to cybersecurity, and earning money as a bug bounty hunter.
#1. Choose a Suitable Bug Bounty Platform
Deciding upon a suitable bug bounty platform for your first bug bounty hunting is crucial. As a beginner, finding a bug bounty platform that’s less competitive and less crowded can help significantly.
Most often, these platforms don’t offer monetary benefits; instead, they offer recognition, points, and reputation rewards—helping you build a credible portfolio. Thus, when you’re just starting out as a bug bounty hunter, you must focus on gaining experience and reputation points instead of running behind bounty money.
The different bug bounty platforms you can sign up for are HackerOne, Synack, Open Bug Bounty, and Bugcrowd.
#2. Create Your Profile
Once you sign up for a suitable bug bounty platform, the next and most crucial step is creating a profile that lets you mention your skills, total years of experience, recommendations, and certifications, if any.
A well-represented and crafted profile can help you attract potential bug bounty-hunting program owners looking for skilled bug hunters.
#3. Review Program Policies
Each bug bounty program comes with its own set of rules, guidelines, and scope of work.
Thus, it’s important to carefully review the bug-hunting program policies and responsible disclosure policy and understand the scope of testing and the rewards for the same.
#4. Choose a Suitable Bug to Work On
Determining a specific bug you want to specialize in hunting is critical, especially as a beginner. Whether you wish to find injection or cross-scripting, focusing on one bug at a time is essential instead of going all in and getting confused.
Finding a bug comes with lots of practice. You won’t be able to do it in one go, and even if you could successfully find a bug, there are chances it has already been found and reported by another bug hunter, and hence, you won’t be rewarded with the bounty.
#5. Learn Bug Reporting and Bug Disclosure
Once you find a bug, there are specific steps to report the bug to the company or the program owner. Different types of bugs come with different severity levels, where the injection bugs have the highest severity.
To report a bug, first, you must mention the location where you found the bug and how the bug can be reproduced. Next, you must mention all the necessary steps you took to identify that bug.
You can also prepare demonstration videos with the help of screenshots to validate your identity and Proof of Concept (POC). In addition, mentioning the reported bug’s impact on the entire application usage and adhering to the company’s responsible disclosure is also crucial.
Lastly, once the program owner reviews and verifies your bug and finds it valid, you’ll receive the determined reward or monetary payment per the program’s policy.
Tips to Practice and Get Better as a Bug Bounty Hunter
Simply acquiring knowledge isn’t enough. You must keep regularly practicing and applying the skills learned to become successful in bug bounty hunting.
Here are some tips for practicing and getting better as a bug bounty hunter:
- Practice on websites and vulnerable applications for online practice, such as DVWA, WASP WebGoat, or Juice Shop that lets you legally practice finding and exploiting vulnerabilities.
- You can also play online games like SecArmy, CTF365, and Hack The Box and capture flags (CTFs). These games are designed as internationally vulnerable and hide flags within the root, which you must identify and exploit to capture the flag.
- Besides practicing online, you can also practice bug hunting offline by downloading VMware or bWAPP on your PC.
Popular Bug Bounty Platforms
HackerOne and YesWeHack are two of the most popular and widely used bug bounty platforms by several ethical hackers across the globe.
Let’s take a quick look at each of these with their features.
#1. HackerOne
HackerOne is one of the leading hosts for bug bounty programs that close the gap between an organization’s assets and their protection.
It provides a bunch of opportunities for ethical hackers to help organizations and businesses close their security loopholes and mitigate bugs and vulnerabilities before they breach the company and harm its reputation.
Through HackerOne, bug hunters and ethical hackers have protected some of the big giants, including PayPal, Zoom, Hyatt, and Nintendo.
As a bug bounty hunter, HackerOne provides an intuitive interface with top security features that facilitate bug bounty hunting. These features include
- Attack surface intelligence helps reckon an organization’s attack surface and monitor and identify risks in its digital assets.
- Prioritized risk with dynamic attack surface management and continual testing to address security risks.
- Adversarial testing by designing a program that suits an organization’s security assessment needs and monitoring the overall security from unified platforms—making it easier to identify flaws before cybercriminals.
- Manage security risks by engaging with the top industrial experts to find risks fast and learn through the process.
Over 1,000 brands globally use HackerOne, and nearly 1,000,000+ ethical hackers use the platform to secure global companies and organizations.
#2. YesWeHack
YesWeHack is a dedicated global bug bounty platform that helps protect organizations with its global community of experts and bug bounty hunters.
For companies, it provides access to a virtually unlimited pool of ethical hackers to maximize their security and testing capabilities. YesWeHack’s bug bounty program complies with the strictest European standards and regulations to secure an organization’s and the bug hunter’s interest.
Organizations can choose from several types of bug bounty programs, including private bug bounty program, public bug bounty program, and on-site program that best matches their security and business needs.
Besides, for bug bounty hunters, it enlists a list of programs available with details like the program description, scope, bounty price range, rewards, and reports.
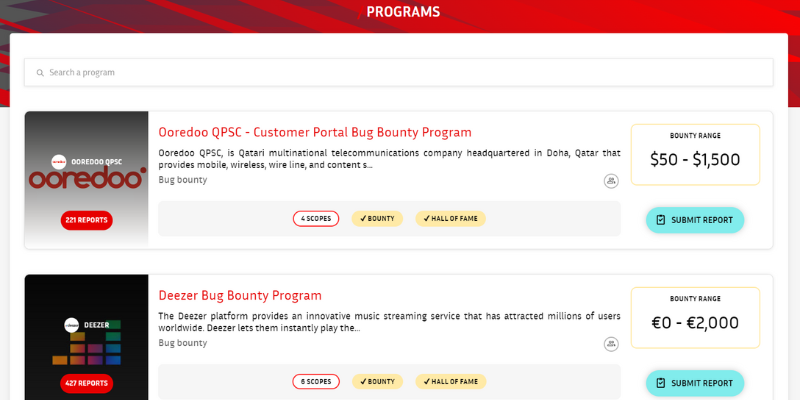
Thus, YesWeHack is a perfect platform to start your journey as a bug bounty hunter by choosing a suitable program of your choice and submitting reports after identifying bugs and vulnerabilities.
Wrapping Up
In today’s digital age, bug bounty hunting has become one of the most critical and credible professions—that’s lucrative for both the bug hunters and the organizations to safeguard their online network and systems.
While it isn’t complex, bug bounty hunting requires certain skills and prerequisites, like the basics of programming, internet, networking, and cybersecurity, to become efficient in the role.
So, if you wish to embark on the journey of becoming a bug bounty hunter—we hope this article helps you. Make sure to learn the prerequisite skills, sign up for several newsletters, stay updated on the bug bounty forums and websites, keep practicing and brushing up on your bug-hunting skills, and sign up to the bug bounty platforms mentioned in the article to get started. All the best!
Next, check out bug bounty platforms for organizations to improve security.
Si quiere puede hacernos una donación por el trabajo que hacemos, lo apreciaremos mucho.
Direcciones de Billetera:
- BTC: 14xsuQRtT3Abek4zgDWZxJXs9VRdwxyPUS
- USDT: TQmV9FyrcpeaZMro3M1yeEHnNjv7xKZDNe
- BNB: 0x2fdb9034507b6d505d351a6f59d877040d0edb0f
- DOGE: D5SZesmFQGYVkE5trYYLF8hNPBgXgYcmrx
También puede seguirnos en nuestras Redes sociales para mantenerse al tanto de los últimos post de la web:
- Telegram
Disclaimer: En Cryptoshitcompra.com no nos hacemos responsables de ninguna inversión de ningún visitante, nosotros simplemente damos información sobre Tokens, juegos NFT y criptomonedas, no recomendamos inversiones