Threat actors leverage web browsers to infiltrate users’ computers or corporate networks. They do so by creating malicious websites that can install malware on users’ computers and cause irreparable damage. But with browser isolation, you can safeguard your web browsing activity to prevent common web-based attacks.
What is browser isolation technology exactly, how does it work, and what are the benefits of using browser isolation? Let’s find out.
What Is Browser Isolation?
Browser isolation, also known as web isolation, is a security solution that contains your browsing activity in an isolated environment like a virtual machine, sandbox, or the cloud, barricading your device from the inherent risk of online browsing.
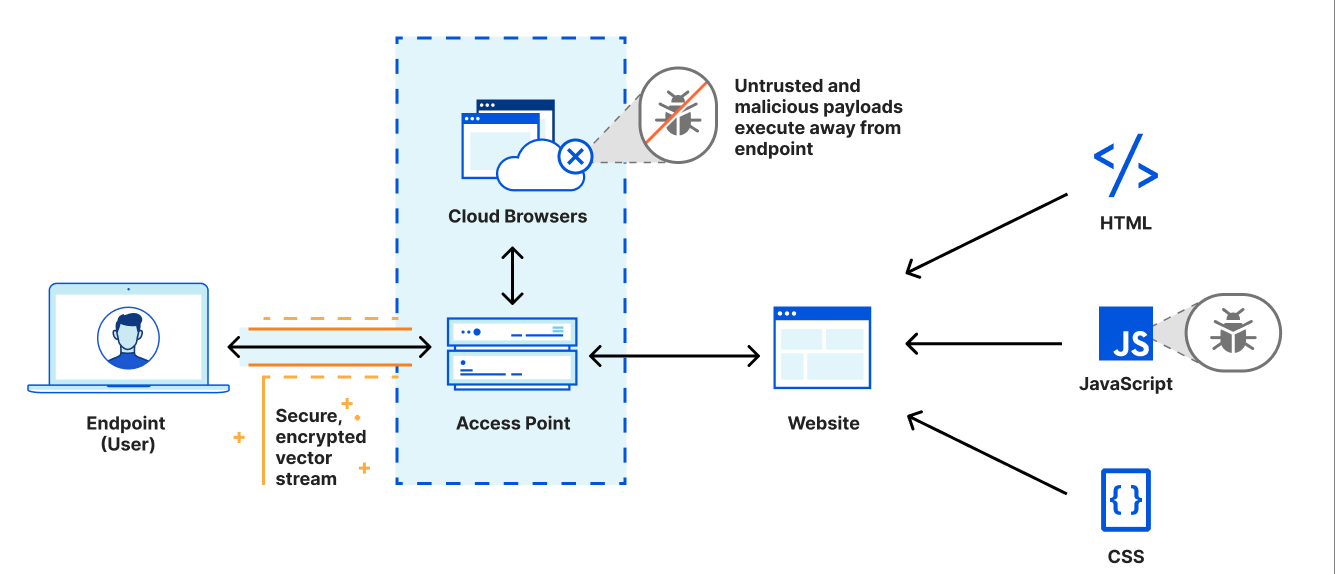
Once you type a website, your browser loads content and code from the website’s server and executes code within your browser. The process seems harmless, but it is not.
A threat actor can create a malicious website or web app riddled with harmful code and share its link with you via phishing attacks. When you reach the malicious site by clicking on the link, the malicious code will automatically get downloaded on your device, infecting your device or network.
Browser isolation provides your device with an additional layer of security by keeping your browsing activity confined to an isolated environment.
How Browser Isolation Works

Browser isolation works by confining browsing activity to an isolated environment. This simply means your web browser runs in its own environment and doesn’t interact with your device’s operating system.
If you come in contact with malware, the malware doesn’t go past the isolated environment. And your device remains safe from malware or other web-based threats.
There are different ways web isolation technologies can work, but the typical process involves the following:
- Remove your browsing activity from your system and run it in a virtual environment or the cloud.
- Automatically delete the browser environment once you end your browsing session. This ensures that malicious content or hidden malicious code found during a session is wiped out at the end of a session.
- When you open the secure virtual browser again, you will get a clean browser free from malware or malicious code.
Browser isolation helps users browse the web as they typically do while protecting their device and corporate network from malware and other online threats.
And the best part is the users will not see any difference. They will see as if the browser is running on their local computers.
Different Types of Browser Isolation
Here are the three types of browser isolation techniques you should know about.
#1. Remote Browser Isolation
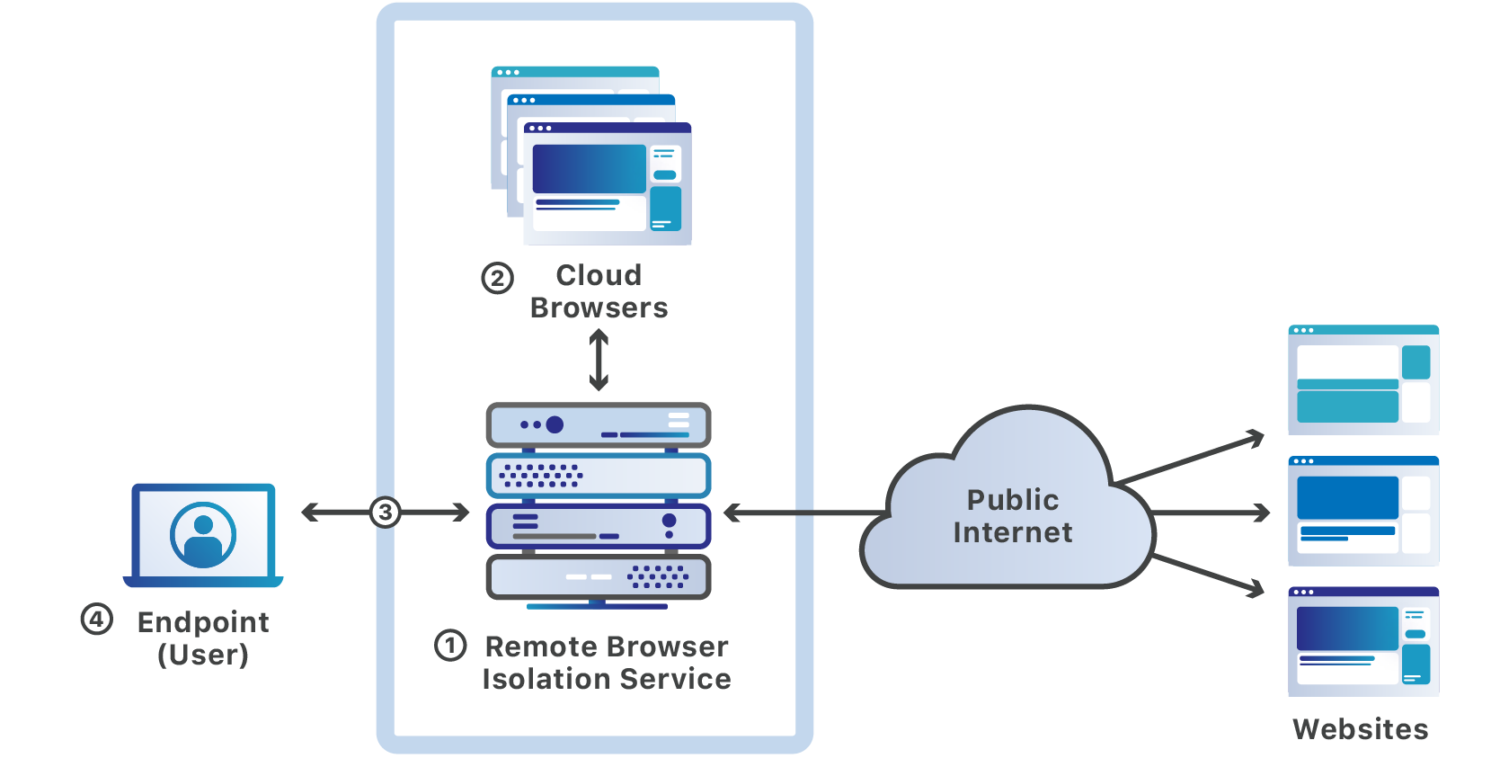
In the remote browser isolation (RBI) technology, a user’s browsing session is hosted on a remote server, away from the user’s device and corporate network.
As RBI loads web pages and executes associated JavaScript code on a cloud server, an organization’s internal network remains protected from malicious content, malicious downloads, and other web-based threats.
Now the question comes-how does remote browser isolation work?
The following are key ways how remote browser isolation technology works:
- The provider offering remote browser isolation services sends users videos or images of their browsing activity. This method is also known as “pixel pushing.” The end users receive only pixels, not any code, so it protects the users’ devices from malicious code execution.
- In this method, remote browser isolation vendors open and rewrite web pages to remove malicious web content before sending it to the users. This technique is called the DOM mirroring technique.
#2. On-Premises Browser Isolation
On-premises browser isolation technology defends users the same way as remote or cloud-hosted browser isolation does. But the difference is browsing activity is hosted on the servers managed by the organizations.
The drawback of on-premises browser isolation is that organizations must provide their own servers for browser isolation, which can be costly.
Also, isolation usually happens within the organization’s firewall. This means end users’ devices are protected from malicious JavaScript, but organizations’ internal networks are always at risk.
Therefore, opting for remote or cloud-based browser isolation is an intelligent choice.
#3. Client-Side Browser Isolation
In the client-side browser isolation method, web pages/web apps load, and associated JavaScript code executes on the users’ devices but in an isolated environment, using sandboxing or virtualization.
The core concept of browser isolation is based on physically preventing harmful code from downloading on the system. But client-side browser isolation actually loads potentially malicious content on the user’s device, though on a virtual machine. So it still poses risks to devices and networks. This is the reason why companies prefer not to implement client-side browser isolation.
Why You Need an Isolated Browser Environment

Most web browsers automatically execute all JavaScript associated with web pages. This means threat actors can employ malicious JavaScript to infiltrate systems and networks.
Here are common threats internet users can mitigate by implementing browser isolation technology.
#2. Drive-By Download Attacks
Threat actors often exploit browser vulnerabilities to install malicious code on users’ devices. Many websites serving malicious ads can also download malicious code to users’ systems. But with browser isolation, malicious code will be downloaded on an isolated environment (remote server) separated from the local machine.
#3. Clickjacking
In simple words, a clickjacking attack tricks users into thinking that they’re clicking on one thing, but they are clicking on another thing in reality. Threat actors employ clickjacking to send web traffic to scam websites, generate fake ad revenue, or download malware on users’ devices.
Virtualized web browsers are often equipped with technology to block much of the malicious code served using advertising and third-party sites.
#4. Malvertising
Threat actors inject malicious code into legitimate ad networks. And when the malicious ads are displayed on the users’ computers, the code will be executed, infecting the users’ devices. But with browser isolation, there no local code execution.
As all code execution happens in an isolated environment, often on the cloud, the local devices stay protected from browser-based attacks.
#5. Cross-Site Scripting
Threat actors inject malicious code into popular websites to install malware on the devices of internet users who visit those websites.
Having browser isolation technology implemented on your device can keep your device safe. This is because the code execution will happen in an isolated environment on the cloud, away from your device.
#6. Phishing Redirection Attacks

Hackers create phishing websites to install malware, steal login credentials, and swindle money.
You visit a phishing website thinking that you are on a legitimate website. But, in reality, the website was set up by a threat actor with malicious intent.
Most reputed browser isolation vendors incorporate state-of-the-art web security technology to block zero-day phishing websites. This prevents you from visiting a phishing website.
#7. On-Path Browser Attacks
Threat actors can view users’ web browsing sessions, distort content, and impersonate the user through an on-path browser attack. As no path to access corporate resources from the browser exists in browser isolation, it can reduce the damage caused by such an attack.
Benefits of Browser Isolation
Here are the key benefits of implementing browser isolation in your company.
Protect From Web-Based Attacks

Keeping your browsing sessions away from your device can prevent web-based attacks like malware, drive-by download, or clickjacking.
Save Time for IT Administrators
Traditionally, IT administrators are likely to blacklist malicious websites to prevent employees from accessing those websites. Also, IT administrators may require to monitor alerts when users open potentially unsafe websites knowingly or inadvertently.
Browser isolation takes this burden off their shoulders. As malicious code cannot go past the isolated environment, there is no need to implement web-filtering solutions.
Improve Productivity
Sometimes, organizations limit web access due to security reasons. For example, employees may not download PDF files or other types of documents due to the risk of hidden malware in such files.
As employees cannot access the web freely, it can hamper their productivity. With browser isolation, employees can safely access the web without restrictions. This, in turn, improves their productivity.
Protect From Phishing

Browser isolation protects users from phishing attacks. As all web-based emails are opened on a remote server, malicious attachments or malicious code don’t reach the local devices.
What’s more, leading browser isolation vendors use state-of-the-art technology to block phishing websites and phishing emails.
Provide Behavior Analytics
By implementing browser isolation technology, companies can gain insights into employees’ web activities. As a result, they can identify insider threats and implement corrective measures.
Reduce the Need for Complex Endpoint Security Solutions
As browser isolation takes browsing sessions on the cloud or in a virtual environment, it prevents malware and other web-based threats from targeting the users’ devices.
Consequently, companies may not need to implement complex endpoint security solutions to protect their endpoints.
How to Pick the Best Browser Isolation Tool
When choosing a browser isolation solution, you need to ensure that it has the following features:
- You should be able to integrate it with popular email clients to offer phishing protection. This will allow all links in your emails to open in an isolated environment on the cloud, ensuring malicious code cannot be downloaded on your device.
- Your chosen browser isolation solution should allow you to configure read-only web pages for suspicious or unknown web pages. This feature will help protect users from credential theft.
- It should allow you to control and manage corporate browsing policies based on user location, URL category, and more.
- The solution must follow the zero-trust architecture and offer you a fast browsing experience.
Also, you should go for a solution that allows you to disable or enable downloading and uploading.
Some reputed browser isolation solutions are Apozy, Silo, Kasm Workspaces, Seraphic Web Security, and Puffin Cloud Isolation.
Browser Isolation and Zero Trust Security Architecture
The zero trust model is a security approach that focuses on verifying everything, trusting none.
In other words, you should not trust users, applications, and web traffic by default. A website a user has already loaded on their system 500 times safely can infect their system when they load it 501 times.
So, to implement the assumption of zero trust security, you must ensure that every website should be checked for malicious content every time it is loaded on your system to keep your system secure. And browser isolation helps you do that.
Browser isolation prevents web-based attacks by keeping browsing activity contained in an isolated environment instead of relying on your employees to depict safe online behavior.
Challenges of Browser Isolation Technology
Browser isolation technology enhances cybersecurity in organizations. But you need to consider some computing and user-experience drawbacks before committing to a browser isolation vendor.
In-Adequate Protection

In the DOM mirroring isolation, certain types of malicious content from web pages are filtered out before sending the remainder of the web pages to the users.
However, sophisticated phishing pages may conceal malicious content as other types of content the browser isolation provider allows. This can open the users’ devices to various web-based attacks.
Limited Website Support
When a browser isolation solution removes malicious content from web pages, as happens in the DOM mirroring technique, it can break certain web pages. As a result, the web pages may not render correctly or at all.
Website owners also frequently make changes to their websites that can break DOM reconstruction functionality.
Slow Speed Due to Latency
When you implement remote browser isolation, all of your employees’ web traffic will be routed through the cloud-based system before being forwarded to them. As a result, there can be some latency in the connection, degrading the user experience.
Insufficient Budget
Implementing remote browser isolation requires companies’ web traffic to be routed through and analyzed on the cloud. And streaming encrypted pixels of web pages to the endpoints demands tons of bandwidth and processing power. So many organizations can find it expensive to deploy these solutions across all employees.
Conclusion
Web browsers are an indispensable tool to access the web. But traditional web browsers cannot offer you optimum protection from web-based attacks, such as phishing, malware, clickjacking, and much more. So you should start using a browser isolation solution in your organization to safeguard your data and systems.
Even if you don’t work in a professional setting, you can reap the same security benefits from using browser isolation. After all, hackers don’t discriminate when it comes to targeting people.
You may also read about the ultimate guide to securing Google Chrome.
Si quiere puede hacernos una donación por el trabajo que hacemos, lo apreciaremos mucho.
Direcciones de Billetera:
- BTC: 14xsuQRtT3Abek4zgDWZxJXs9VRdwxyPUS
- USDT: TQmV9FyrcpeaZMro3M1yeEHnNjv7xKZDNe
- BNB: 0x2fdb9034507b6d505d351a6f59d877040d0edb0f
- DOGE: D5SZesmFQGYVkE5trYYLF8hNPBgXgYcmrx
También puede seguirnos en nuestras Redes sociales para mantenerse al tanto de los últimos post de la web:
- Telegram
Disclaimer: En Cryptoshitcompra.com no nos hacemos responsables de ninguna inversión de ningún visitante, nosotros simplemente damos información sobre Tokens, juegos NFT y criptomonedas, no recomendamos inversiones


