The recent advancements in technology have brought about tremendous innovations to satisfy the needs of modern businesses and users.
Technology, tools, and internet-driven products and services have transformed how we used to work and live. They have simplified our lives and increased convenience in all aspects, whether business or personal life.
However, technology has also presented lots of concerns and cybersecurity risks that can devastate both spheres of our lives.
Businesses have been suffering losses in millions along with customer trust and industry reputation. Similarly, individuals have been under terror due to crimes and threats as a result of exposed personal data.
Hackers and their hacking methods are evolving since they are also skilled professionals. Some use their skills to conduct crimes, whereas some are hired by organizations to combat bad hackers.
And if you want to safeguard yourself and your business from hacks and hackers, it’s pertinent to know about what’s going on in the cybersecurity industry and the types of hacks and hackers.
This article will get to know the different types of hacks and hackers to distinguish them and implement the correct security measures to remain on the safer side.
What Is a Hack?
A hack is an act performed by an individual(s) or hackers to compromise an organization’s security by gaining access to data, networks, systems, and applications and carrying out attacks. The misuse of devices and systems devastates a business in terms of finances and reputation.

A hack originates from a system that is used by a hacker who has coding skills and advanced computer software and hardware.
In modern hacks, hackers are using stealthy methods which are designed to skip the eye of IT teams and cybersecurity software teams to conduct attacks. They can trick users into opening malicious links and attachments, which further results in exposing sensitive information.
Examples of hacks can be deploying virus and malicious code, man-in-the-middle attacks, DDoS, DoS, phishing, ransomware, etc.
Different Types of Hacks
Here are different types of hacks:
Phishing
Phishing is an attempt taken by cybercriminals to steal your identity and money through emails. Hackers make you give up your personal information, including bank credentials, passwords, card details, etc.
The attacker sends an email to a person using tricky words that seem very real. They act like a person you can trust, like an interviewer, bank manager, service associate, and more. It combines with other attacks like code injection, network attacks, and malware to make the hack possible.
There are various types of phishing attacks, such as email phishing, spear phishing, whaling, smishing, vishing, and angler phishing.
DoS and DDoS
A Denial of Service (DoS) attack focuses on a network or machine to shut it down and make it inaccessible to the end-users.

Here, cyberattackers interrupt the functionality of a device by flooding the network or machine with unlimited requests so that normal traffic is unable to access it.
DoS is of two types:
Buffer Overflow attacks: This attack targets CPU time, hard disk space, and memory and consumes all of them to crash the system and affect server behavior.
Flood attacks: This attack targets the servers with a flooding amount of data packets. The attacker oversaturates the server capacity, resulting in DoS. In order to make DoS flood attacks successful, the attacker must have more bandwidth than the targeted machine.
In the DDoS attack, the traffic flooding comes from various sources. This attack is more critical than DoS as you can not shut various sources at a time.
Bait and Switch
Bait and Switch is a technique used by fraudsters to steal personal data and login credentials through trusted ads and avenues. They trick users to visit malicious sites and take all the details under users’ noses.
These attacks mainly form from the advertising space sold by websites. Once the attackers purchase the advertising space, they immediately replace the ad with a malicious link, resulting in locking the browser and compromising systems.
Internet-based content marketing is the main channel for the attacks where users are tricked to open links, which later turns out to be malicious.
Cookie theft is a hijacking tactic where an attacker gets access to user information. Here, a third party copies the insecure session data and uses this to impersonate the user. It generally occurs when a user visits trusted sites through public Wi-Fi or an unprotected network.
Once this happens, the attacker can use the information or account to post false messages, transfer money, or do other malicious things.
It can be prevented if a user uses SSL connections to log in and avoids using unprotected networks to access sites.
Virus, Trojan, Malware

A virus is a computer program that connects to another computer or software program to damage the system. Hackers insert code in the program and wait until someone runs the program. This way, they infect other programs on a computer.
A trojan executes a program that says it is harmless and useful. In reality, it does malicious things just like Trojan Horses were used by the Greeks to attack enemies at night.
Instead of targeting a software system, Trojan targets installing of other malware in the system, resulting in fooling users.
A worm is a similar malware as a virus. It executes malicious payload and self-replicates on computer systems. The only difference is in their spreading technique. A virus wants a host program, but a worm lives in its own independent program. They sometimes are spread by themselves, without any human interference.
Furthermore, there is a variety of other malicious threats, such as ransomware, adware, spyware, rootkits, bots, and a lot more.
ClickJacking Attacks
ClickJacking, which is known as a UI redress attack, targets users through multiple opaque or transparent layers to trick them. Once a user clicks on the button or link without knowing they are clicking on the wrong one, they lose their information to the wrong hands.
Suppose you are visiting a website and scrolling to check the page. Suddenly, when you go to click over some link, you may see some other ads that let you click over that link. Thus, attackers route you to another page. This is how ClickJacking attackers work.
For example, when you visit the www.wyz.com website and see stylesheets or text boxes on the page, you will get free offers and other suitable offers that attract you to open the link. This way, you lose your login credentials and personal information.
Fake WAP

Wireless Access Point (WAP) is a technique used to connect many users at a time through a public channel. Fake WAP means doing the same thing by faking the technique.
Here, a hacker usually chooses a public place where there is free Wi-Fi, such as the airport, shopping centers, and local coffee shops.
Sometimes they set Wi-Fi for the users allowing free access and playing like a ninja. In this case, you freely give all your information during sign-in in the Wi-Fi account and other popular websites. In this way, they also hack your Facebook, Instagram, Twitter, and other accounts.
Keylogger
Keylogger, also called keyboard capture or keystroke logger is a technique used to record every keystroke on a device or computer. It also has software that you can use on your smartphones.
Hackers often use a keylogger to steal login credentials, sensitive enterprise data, and more. It is actually software that records every activity, including mouse clicks. You also find hardware keyloggers where there is a device inserted between CPU and keyboard that provides many features to capture the records.
Hackers use this technique to access your account numbers, pin codes, email ids, passwords, and other confidential.
Eavesdropping
Eavesdropping is an old security threat where an attacker carefully listens to the network’s communications to gain private information, such as routing updates, application data, node identification numbers, and many more.
The hacker uses the data to compromise nodes in disrupting routing, degrading application performance, and networking. Its vectors include email, cellular networks, and telephone lines.
Waterhole Attacks
A waterhole is a computer attack where a hacker observes or guesses the websites that an organization or individual often uses. Attackers then infect those websites through malware, and thus, some members also get infected from this attack.
This technique is harder to detect as hackers look for a specific IP address to attack and get specific information. The aim is to target the user’s system and gain access to the websites at the target.
SQL Injection
SQL injection (SQLi) is an attack where an attacker uses malicious code for database manipulation. This way, they access information kept safe in an organization’s database. They interfere with the application queries to view data, including users’ data, business data, and more.
Once they have access, they can either delete the data or modify it, causing changes to an applications’ behavior. In some cases, the hacker gains administrative rights, which are highly detrimental for an organization.
SQLi targets web applications or websites that use SQL databases like Oracle, SQL Server, MySQL, and more. This is the oldest and most dangerous attack, which once gets successful, enables hackers to access trade secrets, personal data, and intellectual property of a company.
Brute Force Attacks
A brute force attack is an easy way of hacking that focuses on trial and error methods to crack passwords, encryption keys, login credentials, and more. Attackers work through all the possible cases to get the right one.
Here, brute force means hackers use forceful attempts to force their path into private accounts. This is an old method of attack but still is popular and effective with hackers. Hackers gain profit from the ads, steal private data, spread malware, hijack your system for malicious activity, ruin website reputation, and more.
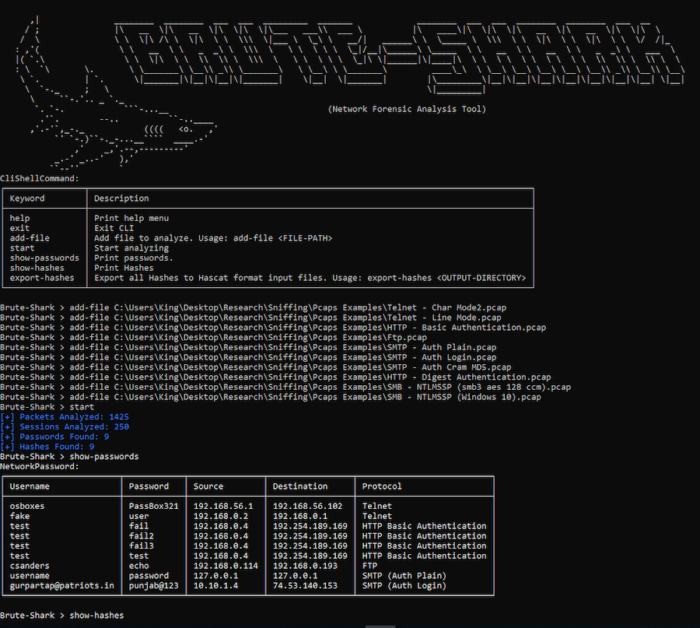
There are different kinds of brute force that attackers are using to gain access. Some are simple brute force attacks, dictionary attacks, hybrid brute force attacks, reverse brute force attacks, and credential stuffing.
DNS Spoofing (DNS Cache Poisoning)
In this, alternative DNS records are being used by an attacker to redirect traffic to a malicious site.
For example, you are new to your college, and your seniors change the classroom numbers. So, you end up in the wrong classroom. This goes on happening until you get the correct campus directory.
DNS spoofing works in the same way. The hacker enters false data into the cache so that DNS queries give you the incorrect response, resulting in entering the wrong websites. This attack comes under a deceptive cyber threat.
Cracking Passwords
Cracking passwords is the way hackers use to get login credentials. A brute force attack is also a password cracking technique.

In this, all the passwords must be stored with Key Derivation Function (KDF). If it is stored as plaintext, the attacker hacking the database gets all the account information. They use various techniques to crack passwords, such as phishing, malware, rainbow attack, guessing, dictionary search, and more.
Who Is a Hacker?

A hacker is a person who has networking, programming, computer, and other skills to solve problems or cause problems.
They break into the computer system to install malware, destroy data, steal information, disrupt devices, and a lot more.
This does not mean that all hackers are bad actors. They can be both good and bad.
In some cases, hacking is used as a legal procedure by legitimate figures in order to secure their systems and data or country.
However, maximum hackers use their technical skills to harm organizations and individuals by stealing or exposing their information, asking for ransom, destroying their image in the industry, and so on.
Hackers break the security wall of an organization to gain unauthorized access into phones, IoT devices, entire computing systems, networks, tablets, and computers. They take advantage of a network or system weakness to enter and launch attacks. These weaknesses are of two types – technical and social.
Different Types of Hackers
You know what hacking is and its types.
But who is behind all this hacking, and how can you identify and differentiate between them?
Since all the hackers are not criminals, let’s understand different types of hackers and differentiate between them.
White Hat Hackers
White Hat hackers are authorized hackers who have the technical knowledge to find vulnerabilities in the networks and systems. They have the right to hack the systems to check security vulnerabilities to stay protected from criminal hackers.
They fix loopholes and weaknesses in the security system and safeguard an organization from data breaches and different types of external and internal attacks.
Black Hat Hackers
Black hat hackers have the same skills as white hat hackers but use them for the wrong purposes. They are called cybercriminals who break into the systems with criminal or malicious intent.
Black hat hackers have advanced skill sets to carry out the possible attacks. They search for the security vulnerabilities and loopholes to carry out the attacks to cause severe damage to an organization in terms of money and reputation.
Gray Hat Hackers

A gray hat hacker is again a security expert who finds an easy way to hack systems and networks. They come between black hat hackers and white hat hackers.
How?
They engage in these activities either to help the website owner know the vulnerabilities or steal information. According to their activities, they are categorized. Some gray hat hackers perform hacking for their enjoyment. They do not have any authorization, but they choose how to use their skills.
Script Kiddies
Script kiddies are also known as amateur hackers as they do not have advanced skills in the field of hacking. They follow the scripts of experienced hackers to hack systems and networks.
Generally, script kiddies perform these activities just to get attention from experienced hackers. They do not have the entire knowledge of the process but enough to flood an IP address with excessive traffic.
For example, script kiddies can hack during Black Friday shopping deals.
Hacktivist
Hacktivists are the group of people who carry out hacktivism activity to target terrorists, pedophiles, drug dealers, religious organizations, and more.
Hacktivists perform certain activities to support political causes. They target the entire organization, or a specific industry that they feel does not align with their practices and views.
Malicious Insider/Whistle-Blower Hacker
A malicious insider is an individual, such as a contractor, former employee, partner, etc., who has access to an organization’s network, data, or system. He intentionally misuses and exceeds their data access limits illegitimately.
They are harder to detect as they have authorized access to data and know all the paths very clearly to execute the hack in a planned way. Cloud security is also compromised due to malicious insiders.
Green Hat Hackers
Green hat hackers are the newbies, or you can say, inexperienced ones in the field of hacking. They are not familiar with the security mechanisms and inner workings of the web.
Green hat hackers lack experience, but they have a deep hunger to learn the techniques to go up in the rank list. They are not necessarily threat actors but can cause harm while practicing their design.
Sometimes, they are dangerous as they do not know the outcomes. These can cause the worst case that can be difficult to resolve.
Blue Hat Hackers
Blue hat hackers are different from other hackers as they do not target an organization’s network and system to steal something. They are revenge seekers who hack computer systems to take personal revenge on an organization.
They use techniques to gain access to various accounts or emails. Once they have the information, they start to exploit the profiles by sending inappropriate messages, etc. Sometimes, ex-employees hack companies’ servers to steal information like confidential data and release all the information to the public to damage reputation.
Red hat hackers are somewhat the same as white hat hackers, but they are not authorized to perform hacking operations. Red hat hackers do everything and take every step to stop black hat hackers or other hackers.
They are known to launch a war against illegal hackers and bring down their servers and resources.
Sometimes they choose an illegal way to plan hacking. In short, red hat hackers do the right thing by following the wrong path. They usually infect the terrible guys’ systems, launch DDoS attacks, and use tools to access the bad hacker’s system to demolish it.
Elite Hackers
Elite hackers are the most skilled hackers in the field of hacking. They choose their path either as a white-hat hacker or a black hat hacker. Breaking into the systems and collecting information is very task for them since they are exceptionally skilled.
Elite hackers write their very own exploits from the skills and understanding they have about the systems. They often use Linux distribution made by themselves according to their needs where they have all the tools for hacking.
Whether it is a Windows Operating System, Unix, Mac, or Linux Operating System, elite hackers are experts in every range.
Cyber Terrorists
Cyber terrorists target the population by shutting down all major infrastructures, such as government operations, transportation, energy, etc. Any cyberattack that harms the population in indirect means is known as cyber terrorism.
They want to achieve ideological or political gains through intimidation or threat. Experienced cyber terrorists can cause massive destruction to the government systems leveraging their skills. They might leave a terror message for further attacks.
Conclusion
Knowing about different hacks and hackers will keep you informed about the current cybersecurity risks. It will also help you distinguish between hackers since they are not bad actors. Thus, you can take suitable security measures at the right time to prevent attacks and minimize risks.
Si quiere puede hacernos una donación por el trabajo que hacemos, lo apreciaremos mucho.
Direcciones de Billetera:
- BTC: 14xsuQRtT3Abek4zgDWZxJXs9VRdwxyPUS
- USDT: TQmV9FyrcpeaZMro3M1yeEHnNjv7xKZDNe
- BNB: 0x2fdb9034507b6d505d351a6f59d877040d0edb0f
- DOGE: D5SZesmFQGYVkE5trYYLF8hNPBgXgYcmrx
También puede seguirnos en nuestras Redes sociales para mantenerse al tanto de los últimos post de la web:
- Telegram
Disclaimer: En Cryptoshitcompra.com no nos hacemos responsables de ninguna inversión de ningún visitante, nosotros simplemente damos información sobre Tokens, juegos NFT y criptomonedas, no recomendamos inversiones