Setting an account lockout threshold can prevent hackers from carrying out brute-force attacks to guess user accounts’ passwords. But now hackers are increasingly turning to password spraying attacks to get around login attempt lockout settings.
Compared to a traditional brute force attack, a password spraying attack is relatively simple to execute and has a low detection rate.
So what is a password spraying attack actually, how does it work, how can you prevent it, and what should you do to remediate a password spraying attack? Let’s find out.
What Is a Password Spraying Attack?

A password spraying attack is a type of cyberattack in which threat actors spray commonly used passwords across several accounts in an organization, expecting that some passwords will help them gain access to user accounts.
Hackers use a single, commonly used password against multiple accounts in a company. If they don’t get access to any account on the first attempt, they will move to a different password to carry out password spraying after a few days.
They repeat the process until they get access to a corporate account. As they don’t use multiple passwords against a single account over a short time, login attempt lockout settings don’t block the accounts due to excessive failed attempts.
Once inside a corporate network, they can carry out various activities to meet their malicious objectives.
Users have multiple accounts these days. Creating a strong password for each account is a cumbersome task, let alone remembering those passwords.
So, many users create easy passwords to make the process easier. But easy passwords are popular and well-known. Anyone can google for the most common passwords and get the list of the most used passwords. This scenario has fueled the growth of password spraying attacks.
Digital workspace and enterprise networks vendor Citrix confirmed that threat actors got access to the company’s internal network vis password spraying effort during October 13, 2018, and March 8, 2019.
Microsoft also validated password spraying attacks against more than 250 Office 365 customers.
How Does a Password Spraying Attack Work?
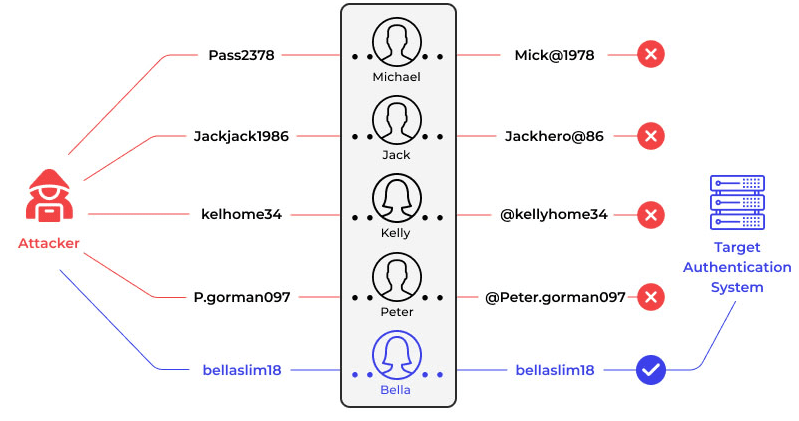
Here are the three steps of successful password spraying attacks.
#1. Collect the List of Usernames
The first step to carrying out a password spraying attack is to get hands on a list of usernames in an organization.
Usually, companies employ a standardized convention for usernames, making users’ email addresses their default usernames for associated accounts. It takes little effort to guess the email addresses of users, as the most commonly used email format is firstname.lastname@companyname.com.
Threat actors can also learn about users’ email addresses by visiting the company’s website, employees’ LinkedIn profiles, or other relevant online profiles.
Alternatively, they can buy a readily available list of usernames from the dark web.
#2. Spray Passwords
Once they have a list of usernames, they will look for “the list of most common passwords.” Google and Bing searches can quickly provide hackers with a list of common passwords for a given year. To increase the chance of their success, hackers may tweak the list of commonly used passwords according to users’ geographical location.
For example, they can take popular sports teams/players, cultural activities, music, and so on into account. If an organization is based out of Chicago, hackers may combine Chicago Bears with commonly used passwords to spray passwords.
After spraying a single password against multiple accounts, they will wait for at least 30 to 50 minutes before starting the next spraying attack to avoid account lockouts.
Hackers can use various automated tools to automate the spraying process.
#3. Get Access to Accounts
If the spraying attack is successful, the attacker will get access to users accounts. Based on the privileges of those compromised accounts, the attackers can do various malicious activities, such as installing malware, stealing sensitive data, making fraudulent purchases, and so on.
Also, suppose the attacker is able to get inside the corporate network. In that case, they can dig deeper into your network via lateral movement to search for high-value assets and increase their privileges.
Password Spraying vs. Credential Stuffing vs. Brute Force Attack
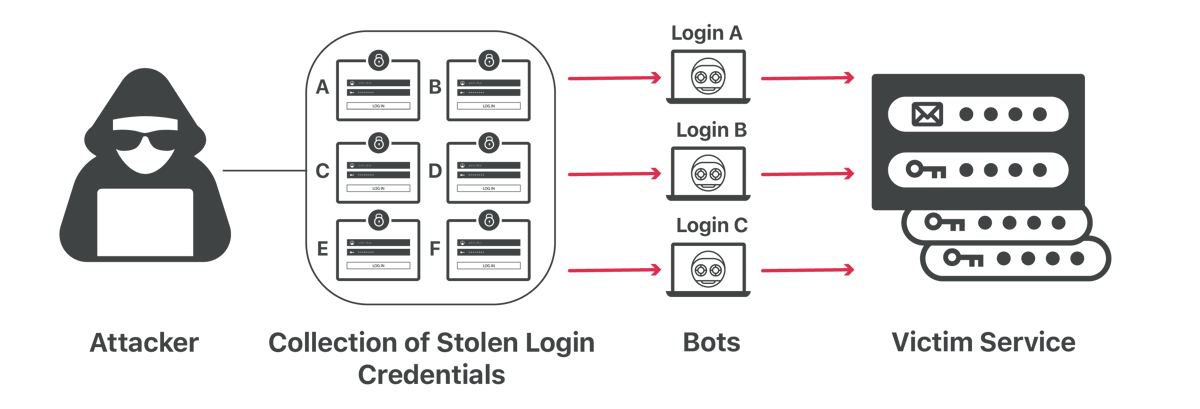
In password credential stuffing attacks, threat actors use stolen credentials from one organization to access user accounts on various platforms.
Threat actors take advantage of the fact that many people use the same usernames and passwords to access their accounts on multiple websites. As more login credentials are getting exposed due to the growing incidents of data breaches, hackers now have more opportunities to carry out credential-stuffing attacks.
On the other hand, a brute-force attack makes use of trial and error to crack passwords and login credentials. Cybercriminals try to guess the correct passwords by testing a wide range of combinations. They use brute-force attack tools to speed up the process.
Login attempt lockout settings can prevent brute-force attacks, as the accounts in question will be blocked once the system detects too many failed login attempts in a short time.
In password spraying attacks, hackers try a single commonly used password against multiple accounts in an organization. As threat actors don’t try various passwords on a single account in a short time, password-spraying attacks can skirt login attempt lockout settings.
How Password Spraying Can Affect Your Company

Here is how a successful password spraying attack can impact your company:
- By gaining unauthorized access to your accounts in your organization, threat actors can expose sensitive information, financial records, customer data, and trade secrets.
- Threat actors might use compromised accounts to make fraudulent transactions, unauthorized purchases, or even siphon money from your business accounts.
- Once hackers gain unauthorized access to user accounts in your company, they can encrypt crucial data and ask for ransom in exchange for the decryption key.
- A password spraying attack can cause a data breach, which can result in financial and reputational loss to your company. Data breach incidents are likely to cause customer trust erosion. As a result, they can take their businesses to your competitors.
- You will need resources to respond to a data breach, get legal counsel, and hire outside cybersecurity experts. So, password spraying will cause a significant resource drain.
In a nutshell, a successful password spraying attack will have a cascading effect on various aspects of your business. This can include financial, operational, legal, and reputational consequences.
How To Detect Password Spraying Attacks

Here are key telltale signs of a password spraying attack:
- You notice a high volume of login activity in a short time.
- There is a high volume of rejected passwords against multiple accounts in a brief time.
- You observe login attempts from non-active or non-existent users.
- There are login attempts from IP addresses that are geographically inconsistent with the known location of the users.
- Attempts are made to access multiple accounts during odd hours or outside your business hours. And one password is being used to log in to those accounts at a time.
You should review authentication logs for system and application login failures of valid accounts to detect password spraying attacks.

If you suspect that hackers are attempting a password spraying attack, here are action points to follow:
- Instruct your employees to change all passwords immediately and enable MFA if any of them haven’t done so far.
- Deploy an Endpoint Detection and Response (EDR) tool to track any malicious activity in your company’s endpoints to prevent the lateral movement of hackers in the event of a password spraying attack.
- Check for the signs of data theft or data encryption and make a plan to restore data from the backup after making sure that all accounts are secure. Deploy a data security solution to safeguard your data.
- Enhance the sensibility of your security products to identify failed login attempts across multiple systems.
- Review events logs to understand what happened, when it happened, and how it happened to improve your incident response plan.
Hackers try to exploit software vulnerabilities in order to elevate their privileges. So make sure your employees install all software updates and patches.
How To Prevent Password Spraying Attacks
The following are some strategies to prevent hackers from gaining access to user accounts by means of password spraying attacks.
#1. Follow a Strong Password Policy

Password spraying attacks target weak passwords that are easy to guess. Implementing a strong password policy will force your employees to create strong, complex passwords that hackers cannot guess or find online. As a result, user accounts in your organization will be protected from password spraying attacks.
Here are the key points your password policy should incorporate:
- Passwords should be at least 12 characters long, including uppercase letters, lowercase letters, and special characters.
- There should be a password deny list, meaning users should not include their dates of birth, places of birth, job titles, or names of loved ones in their passwords.
- All passwords should expire after a certain period of time.
- All users must create different passwords for different accounts.
- There should be an account lockout threshold to block user accounts if multiple unsuccessful login attempts occur.
Implementing a good password tool can help users create strong passwords and avoid using the most common passwords.
Top-rated password managers can help you determine if your passwords are exposed in any data breach.
#2. Enforce Multi-factor Authentication (MFA)

Multi-factor authentication (MFA) adds an additional layer of security to accounts. When enabled, MFA requires users to submit one or more verification factors in addition to usernames and passwords before granting them access to online accounts.
By implementing multi-factor authentication in your company, you can protect online accounts from brute-force attacks, dictionary attacks, password spraying attacks, and other types of password attacks. This is because threat actors won’t have access to additional verification factors sent via SMS, emails, or password authenticator apps.
Furthermore, multi-factor authentication can prevent your online accounts from keylogger attacks.
#3. Implement Passwordless Authentication

Passwordless authentication makes use of biometrics, magic links, security tokens, and more to authenticate users. As passwords are not used to access accounts, hackers won’t be able to carry out password spraying attacks.
So, passwordless authentication is a foolproof way to prevent most password attacks. You can explore these passwordless authentication solutions to secure accounts in your company.
#4. Test Preparedness by Carrying Out Simulated Attacks
You need to check your employees’ preparedness to fight password spraying attacks by carrying out a simulated password spraying attack. This will help you better understand your password security posture and take the necessary steps to enhance password security in your company.
#5. Have a Login Detection Tool in Place
You should set up a real-time auditing tool to detect suspicious login attempts. The right tool can help you identify suspicious login attempts to multiple accounts from a single host over a short time, login attempts on multiple inactive accounts, numerous login attempts outside your business hours, and so on.
Once you discover any suspicious login activity, you can take remedial actions to block unauthorized attempts to access your accounts. These actions can include blocking compromised accounts, changing fireball settings, enabling multi-factor authentication, etc.
#6. Train Your Employees

Your employees play a crucial role in protecting users’ accounts from password spraying attacks. All technical security controls, regardless of how good they are, will not work if your employees don’t create strong passwords and enable multi-factor authentication on their accounts.
So run cybersecurity awareness programs regularly to educate your employees about various password attacks and how to prevent them. Make sure they know how to create a sufficiently complex password.
Conclusion
A password spraying attack can cause severe damage to your company, including account compromise, data breach, and future cybersecurity attacks. So you should increase your password security in your company.
Enforcing a strict password policy, implementing MFA, adopting passwordless authentication, having a login detection tool in place, and training your employees can help you prevent password spraying attacks.
You should also try to be creative while picking your company’s username convention. Stop using the usual one—firstname.secondname@companyname.com.
To enhance accounts’ security in your company, you can explore these magic link platforms for passwordless authentication.
Si quiere puede hacernos una donación por el trabajo que hacemos, lo apreciaremos mucho.
Direcciones de Billetera:
- BTC: 14xsuQRtT3Abek4zgDWZxJXs9VRdwxyPUS
- USDT: TQmV9FyrcpeaZMro3M1yeEHnNjv7xKZDNe
- BNB: 0x2fdb9034507b6d505d351a6f59d877040d0edb0f
- DOGE: D5SZesmFQGYVkE5trYYLF8hNPBgXgYcmrx
También puede seguirnos en nuestras Redes sociales para mantenerse al tanto de los últimos post de la web:
- Telegram
Disclaimer: En Cryptoshitcompra.com no nos hacemos responsables de ninguna inversión de ningún visitante, nosotros simplemente damos información sobre Tokens, juegos NFT y criptomonedas, no recomendamos inversiones



