As data flows ceaselessly across enterprise networks and systems, so does the risk of cyber threats. While there are many forms of cyber attacks, DoS and DDoS are two types of attacks that function differently in terms of scale, execution, and impact but share similar objectives.
We will shed light on the distinctions between these two types of cyber attacks to help you safeguard your systems.
What is a DoS Attack?
A Denial of Service DoS attack is an attack that is carried out on a service aimed at causing a disruption to the normal function or denying other users access to that service. This could be by sending more requests to a service than it can handle, making it slow or broken.
The essence of DoS is to flood a target system with more traffic than it can handle, with the sole aim of making it inaccessible to its intended users. A DoS attack is usually carried out on a single machine.
What is a DDoS Attack?

A Distributed Denial of Service DDoS is also similar to a DoS attack. The difference, however, is that DDoS uses a collection of multiple connected online devices, also known as botnets, to flood a target system with excessive internet traffic to disrupt its normal function.
DDoS function like an unexpected traffic jam clogging the highway, preventing other vehicles from reaching their destination on time. An enterprise system prevents legitimate traffic from reaching its destination by crashing the system or overloading it.
Main Types of DDoS Attacks
Various forms of DoS/DDoS attacks show up alongside the advancement of technology, but in this section, we will look at the major forms of attacks that exist. Widely these attacks come in the form of attacking a network’s volume, protocol, or application layer.
#1. Volume-based attacks

Every network/service has an amount of traffic it can handle at a given period. Volume-based attacks aim to overload a network with a bogus amount of traffic, making the network unable to process any more traffic or become slow for other users. Examples of this type of attack are ICMP and UDP.
#2. Protocol-based attacks
Protocol-based attacks aim to overpower server resources by sending large packets to target networks and infrastructure management tools such as firewalls. These attacks target the weakness in layers 3 and 4 of the OSI model. SYN flood is a type of protocol-based attack.
#3. Application layer attacks
The application layer of the OSI model generates the response to a client’s HTTP request. An attacker targets layer 7 of the OSI model responsible for delivering these pages to a user by sending multiple requests for a single page, making the server occupied with the same request and becomes impossible to deliver the pages.
These attacks are difficult to detect because a legitimate request cannot be easily differentiated from an attacker’s request. The type of this attack includes slowloris attack and an HTTP flood.
Different Types of DDoS Attacks

#1. UDP attacks
User Datagram Protocol (UDP) is a type of connectionless communication with a minimal protocol mechanism used primarily on real-time applications where a delay in receiving data cannot be tolerated, e.g., video conferencing or gaming. These attacks happen when an attacker sends a large number of UDP packets to a target making the server unable to respond to legitimate requests.
#2. ICMP flood attacks
Internet Control Message Protocol (ICMP) flood attacks are a type of DoS attack that sends an excessive number of ICMP echo request packets to a network, leading to network congestion and wastage of the network bandwidth leading to a delay in response time for other users. It could also lead to a complete breakdown of the network/service being attacked.
#3. SYN flood attacks
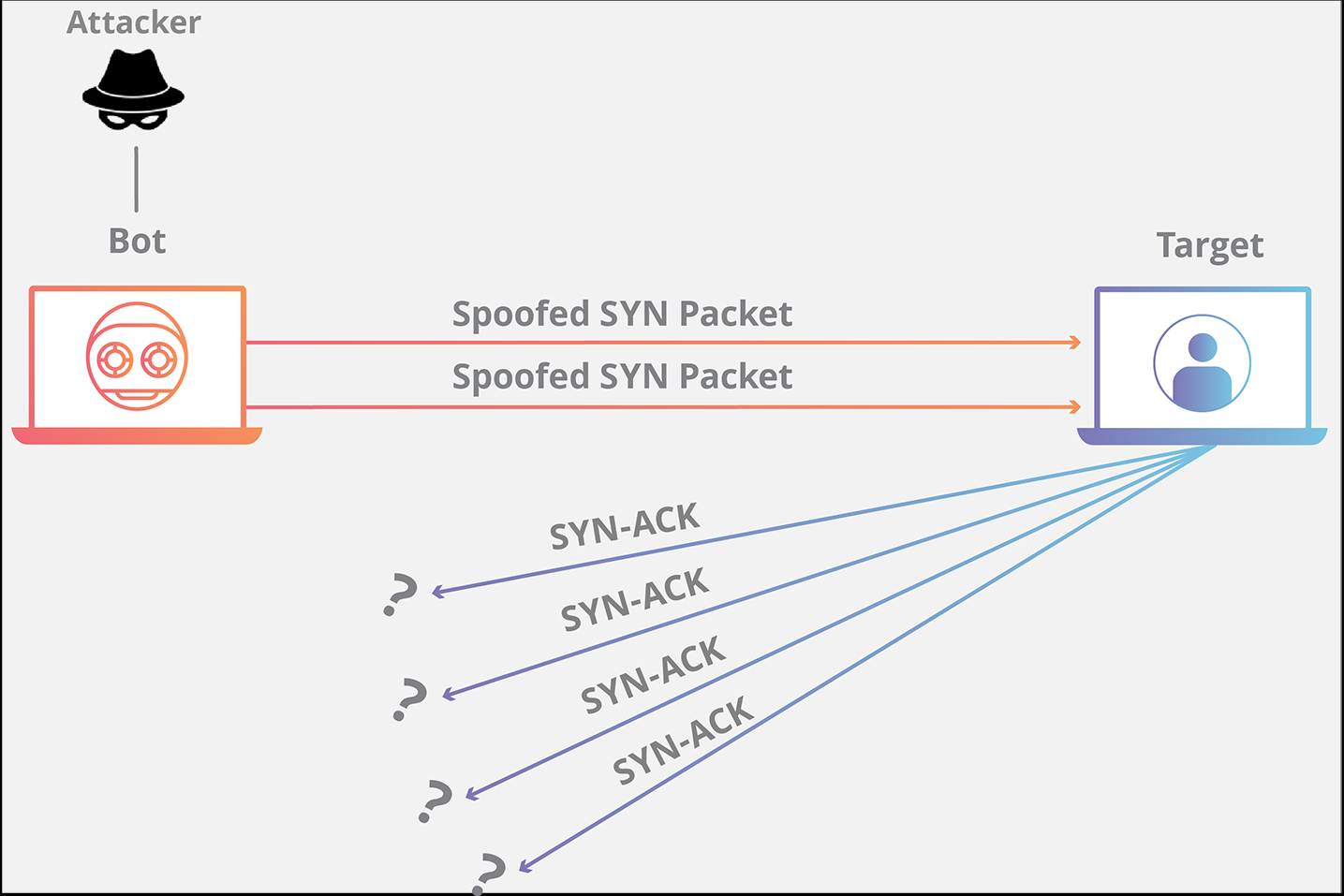
This type of attack can be explained by a waiter in a restaurant. When a customer places an order, the waiter delivers the order to the kitchen, and then the kitchen fulfills the customer’s order, and the customer is served in an ideal scenario.
In an SYN flood attack, a single customer keeps placing order upon order only after receiving any of their previous orders till the kitchen is too congested with so many orders and not able to fulfill anyone else orders. SYN floods attack exploit weaknesses in TCP connection.
The attacker sends multiple SYN requests but does not respond to any of the SYN-ACK responses making the host continuously wait for a response from the request tying up resources until no order request can be made to the host.
#4. HTTP flood Attacks
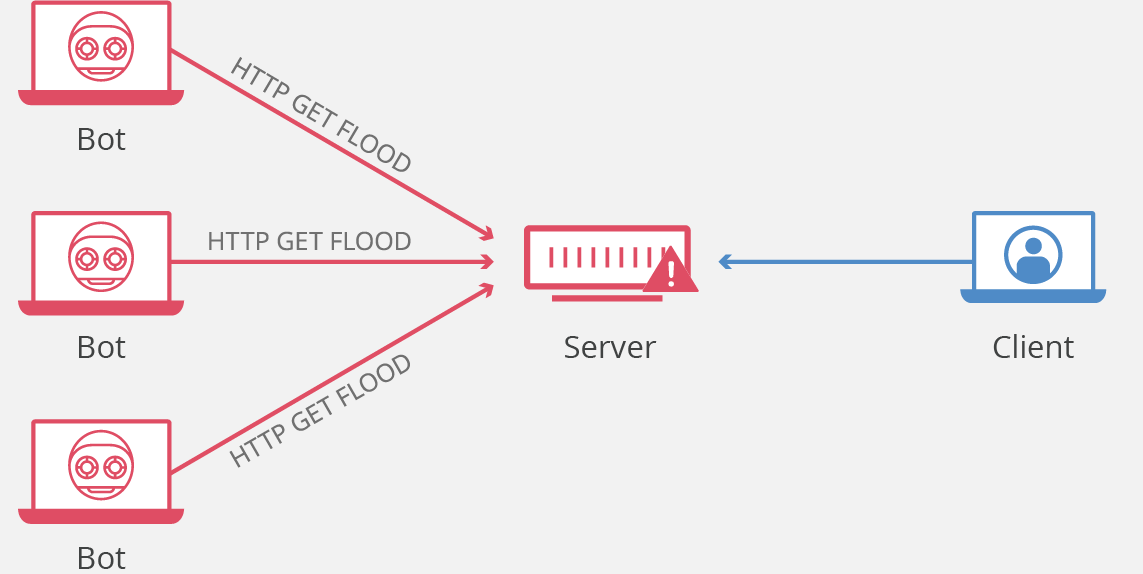
One of the commonest and simplest methods of this attack is the HTTP flood attack, which is carried out by sending multiple HTTP requests to a server from a different IP address. The aim of these attacks is to consume the server’s power, network bandwidth, and memory with legitimate-looking requests making it inaccessible for actual users’ traffic.
#5. Slowloris attack
A slowloris attack is carried out by establishing multiple partial requests to a target, keeping the server open to the connection, waiting for the full request that never gets sent, overflowing the maximum permitted connection allowed, and leading to a denial of service for other users.
Other attacks include ping of death POD, amplification, teardrop attack, IP fragmentation attack, and flooding attack, amongst others. The goal of this attack is to overload the service/server, limiting it from being able to process legitimate requests from legitimate users.
Why do DoS attacks happen?

Unlike other attacks that focus on getting data from the server, DoS attacker aims to hinder the server by using up its resources, making it unresponsive to legitimate users’ requests.
With more technological advances, more businesses are serving customers using the cloud via the web. For enterprises to maintain an edge in today’s market space, it is almost indispensable for them to have a web presence. On the other hand, competitors could leverage DDoS attacks to discredit their competition by shutting down their services, making them look unreliable.
DoS attacks could also be used as ransomware by attackers. Overflooding a business server with irrelevant requests and asking the business to pay a ransom before they call off their attacks and make the server accessible to legitimate users.
Some groups have also targeted platforms that do not agree with their ideologies for either political or social reasons. Overall, DoS attacks do not have permission to tamper with the data on the server; rather, they can only shut down the server from being used by other users.
Mitigating DoS/DDoS Attacks

Knowing that there is a possibility of being attacked, businesses should ensure that they put in measures to ensure that their systems/servers are not easily vulnerable to this attack without putting up a fight. Here are some measures companies can take to ensure they are safe.
Monitor your traffic
Understanding your network traffic can play a huge role in mitigating DoS attacks. Every server has a pattern of traffic that it receives. A sudden spike on the high side, away from the regular traffic patterns, indicates the presence of irregularity, which could also be a DoS attack. Understanding your traffic could help you act fast in cases like this.
Rate limiting
By limiting the number of requests that can be sent to a server/network within a particular time, DoS attacks can be mitigated. Attackers will usually send multiple requests simultaneously to overflood the server. With a rate limit in place, when the permitted amount of requests is received within a particular time frame, the server will automatically delay the excess request making it difficult for the DoS attacker to overflow the server.
Distributed server
Having distributed server in a different region is a global best practice. It also helps mitigate DoS attacks. If an attacker launches a successful attack on a server, the other enterprise servers will not be affected and can still service legitimate requests. Using a content delivery network to cache servers in different locations near users also serves as a layer of prevention against DoS attacks.
Prepare a DoS/DDoS attack plan

Being prepared for any form of attack is key to reducing the amount of damage that the attack can cause. Every security team should have a step-by-step actionable plan on what to do when an incident occurs to avoid looking for solutions within an attack. The plan should include what to do, who to go to, how to maintain legitimate requests etc.
Monitoring your system
Continuous monitoring of the server for any abnormality is very important for all-around safety. Real-time monitoring help to easily detect attacks on time and address them before they escalate. It also helps the team know what regular and abnormal traffic is from. Monitoring also helps to block IP addresses sending in malicious requests easily.

Another means of mitigating DoS/DDoS attacks is by leveraging web application firewall tools and monitoring systems that have been built to detect and prevent the occurrence of a successful attack quickly. These tools are automated to serve this function and can provide all-around real-time security.
Sucuri
Sucuri is a web application firewall (WAF) and intrusion prevention system (IPS) for websites. Sucuri blocks any form of DoS attack targetted at layers 3, 4, and 7 of the OSI model. Some of its key features include proxy service, DDoS protection, and fast scanning.
Cloudflare
Cloudflare is one of the most highly rated DDoS mitigation tools. Cloudflare also offers content delivery networks CDN as well as three layers of protection, website DDoS protection(L7), application DDoS protection(L4), and network DDoS protection(L3).
Imperva
Imperva WAF is a proxy server that filters all incoming traffic sends and ensures they are safe before passing it over to the web server. Proxy service, security patching, and site availability continuity are some of the key features of Imperva WAF.
Stack WAF
Stack WAF is easy to set up and helps with precise threat identification. Stack WAF provides application protection, including website, APIs, and SaaS products, content protection, and application layer DDoS attack protection.
AWS Shield
AWS Shield monitors traffic in real-time by looking at flow data to detect suspicious traffic. It also uses packet filtering and traffic prioritization to help control traffic through the server. It is worth noting that the AWS shield is only available within the AWS environment.
We have reviewed some practices that could help mitigate a successful DoD/DDoS attack on a server. It is important to note that no signs of threats/abnormalities should be dismissed without being properly handled
DoS vs. DDoS Attacks
DoS and DDoS on the surface level are a lot similar. In this section, we will cover some of the notable differences that distinguish them apart from each other.
| Parameter | DoS | DDoS |
| Traffic | DoS comes from a single origin. Hence the amount of traffic it can generate is relatively low compared to DDoS | DDoS attack employs multiple bots/systems, which means it can cause a large amount of traffic from different origins simultaneously and overflow a server quickly |
| Source | Single system/bot | Multiple systems/bot at the same time |
| Mitigation | DoS attacks are easier to detect and terminate since they come from a single origin. | DDoS attacks have multiple origins making it difficult to identify the source of all the targets and terminate the attack |
| Complexity | Easier to execute | Requires large resources and a bit of technical know-how |
| Speed | Slow compared to DDoS | DDoS attacks are very fast |
| Impact | Limited impact | Extreme impact on system/server |
Bottom Line
Organizations should ensure that the security of their system is prioritized in every case; a breach/break in services could lead to a potential loss of trust from users. DoS and DDoS attacks are all illegal and harmful to the target system. Hence all measures to ensure that these attacks can be detected and managed should be taken seriously.
You may also explore top cloud-based DDoS protection for small to enterprise websites.
Si quiere puede hacernos una donación por el trabajo que hacemos, lo apreciaremos mucho.
Direcciones de Billetera:
- BTC: 14xsuQRtT3Abek4zgDWZxJXs9VRdwxyPUS
- USDT: TQmV9FyrcpeaZMro3M1yeEHnNjv7xKZDNe
- BNB: 0x2fdb9034507b6d505d351a6f59d877040d0edb0f
- DOGE: D5SZesmFQGYVkE5trYYLF8hNPBgXgYcmrx
También puede seguirnos en nuestras Redes sociales para mantenerse al tanto de los últimos post de la web:
- Telegram
Disclaimer: En Cryptoshitcompra.com no nos hacemos responsables de ninguna inversión de ningún visitante, nosotros simplemente damos información sobre Tokens, juegos NFT y criptomonedas, no recomendamos inversiones

