As cybersecurity concerns continue to expand, protecting your servers that host business applications and software solutions are essential.
These systems contain crucial information, including your sensitive business and customer data, that you would never want to get leaked. Because if it does, it may impact your reputation, customer trust, and finances.
But safety in the age of ever-evolving cyber attacks is a challenge. Attackers have become way smarter and more inventive, deploying new methods to cause harm for their gains. And most of the time, people and businesses are not prepared enough to take the attacks head-on.
A shocking study by Cyberint says that more than 77% of companies don’t have a cybersecurity incident response plan.
So, if you don’t have any security plans, your business is at greater risk.
Hence, the latest security tools and effective strategies are a must for businesses these days. But most importantly, you must know your current security posture, whether your servers are vulnerable and exposed to cyberattacks or not.
In a situation like this, vulnerability assessment tools, such as Nessus, can help you evaluate your servers’ security status. And if anything goes wrong, you can take action in time and prevent cyberattacks.
This article will help you understand all about vulnerability scanning and how using a vulnerability scanning tool can help you.
What’s Vulnerability Assessment?

Vulnerability assessment refers to the process of evaluating security issues and weaknesses in your IT systems software solutions. This process involves detecting security vulnerabilities, analyzing them thoroughly, and fixing them to prevent risks.
Conducting vulnerability assessment of your network, servers, and systems helps you analyze your security posture and prioritize identified threats based on risks.
Using this information, you can create a plan to resolve the weaknesses and prevent cybercrimes such as data breaches, hacking, privilege escalation due to insecure authentication, password theft, and so on.
However, performing the overall vulnerability assessment, prioritization, and remediation process can be time and resource-intensive. But you can’t wait so much while your security is at stake.
To this, vulnerability assessment tools such as Nessus can help you automate this task with efficiency and accuracy.
Vulnerability assessment tools are software that can automatically scan for existing and new security threats underlying your applications, systems, and servers. They can be of various types:
- Network scanners to detect vulnerabilities and warning signals such as suspicious data packet generation, spoofed packets, unknown IT addresses, etc., in networks
- Protocol scanners to find vulnerable network services, ports, and protocols
- Web application scanners to test and simulate cyberattack patterns
It is essential to conduct regular vulnerability scanning of your applications, network, Linux and Windows servers, etc. But it is not a one-time process; you must continuously scan to stay updated with the risks and remediate them sooner to protect your systems and data.
How Can Nessus Help with Vulnerability Assessment?

Nessus by Tenable provides a gold-standard vulnerability assessment to help you detect security issues and disrupt the attack paths. It is trusted by over 30k organizations globally with 2+ million downloads.
Nessus has one of the broadest and deepest vulnerability coverage along with the lowest rate of false positives with six-sigma accuracy. They have been in the industry for more than 20 years and are continuously striving to optimize the platform by working on community feedback.
Features of Nessus
Nessus was designed with a deep understanding of security. Its impressive features are built to simplify and ease the vulnerability assessment process so you can find issues faster and resolve them in time.
Here are some of the features of Nessus:
Cross-platform Deployment
You can deploy Nessus on any platform, including Linux, Windows, Raspberry Pi, and so on. This vulnerability assessment solution is versatile and portable everywhere, no matter where you are located and how distributed the IT environment is.
Intuitive Navigation
Nessus has intuitive navigation to help simplify your security-related tasks. You can view your security posture easily in one place using the dashboard. It will also be easy to move around and check whether everything is working optimally or has a weakness. This way, the detection and remediation process becomes more manageable.
Resource Center
You also have a resource center where you can read actionable tips on security and guidance on the implementation phase. This helps increase user experience and greater confidence in solving problems and getting better results than operating underwater with guesswork.
Dynamically-Complied Plugins

You will get dynamically-complied plugins to help improve scan efficiency and performance. As a result, the first scan will be completed faster, and you will have time to analyze and respond to cyber threats.
Greater Visibility on Issues
Nessus provides wide coverage on various types of threats and attack patterns so you can identify vulnerabilities quickly. This will help understand and prioritize risks and treat them easily.
With Nessus, you can identify security issues like weaknesses and misconfigurations throughout your organizational assets, systems, and servers.
Pre-Built Templates and Policies
Nessus provides you with 450+ prebuilt templates to help analyze vulnerability quickly. You can use the policies and customize them to accelerate the audit process and stay compliant with industry and government regulations.
Live Results
You can perform automatic vulnerability assessments offline using plugin updates. Next, you can run scans easily to verify any vulnerability lurking in your server or systems. This helps increase detection accuracy and lets you prioritize issues according to the risk vector.
Troubleshooting and Customizable Reporting
Nessus allows you to customize vulnerability assessment reports according to your preferences and meet your organizational needs. In addition, you can export these reports in your rereferred format.
This will not only ease your vulnerability analysis phase but also helps you troubleshoot them without confusion or delays. You will also be able to manage incidents faster by automatically sending vulnerability details to your current SIEM. This will enable you to enrich your event data, inform responses, and prioritize events.
Grouped View
You will get an option to categorize similar vulnerability categories into groups and then present them together in a single thread. This simplifies the research and analysis processes so you can effectively plan for remediation.
How Does Nessus Work?

Nessus helps identify and manage security vulnerabilities so you can close the gaps and enhance your organization’s security posture. The vulnerability assessment and management process with Nessus involves the following steps:
Step 1: Identity
The first step to ensure your servers and systems are protected is to find out the underlying issues. This step requires you to scan all your assets, whether in on-premises or cloud or one place or multiple.
Although this is a challenging process, Nessus makes it more straightforward. It offers comprehensive visibility on your entire IT environment with deep insights. It can cover 47k+ unique organizational assets, including IT, OT, operating systems, IoT, devices, applications, servers, and more. Since it is portable, you can scan your systems no matter where you are.
Step 2: Evaluate
Once you run Nessus’s vulnerability assessment, it will efficiently detect all the weaknesses, misconfigurations, and other issues and potential threat vectors in your network for you to evaluate.
This step gives you an upper hand over the attackers who are trying to infiltrate your systems and servers.
You can use prebuilt templates and target your scanning efforts according to your security posture to get started quickly. Through live updates, you can immediately know as soon as a weakness is found.
Step 3: Comply
Regulatory compliance has become necessary if you want to operate without risks or penalties. Nessus helps with that by keeping you compliant with industry and government regulations. It can audit against 120+ CIS benchmarks and an extra 450 configuration and compliance templates.
Step 4: Analyze
After scanning and detecting issues, you must analyze them to gain powerful insights. Nessus offers advanced groupings and filtering to help collect and analyze results faster and understand your security posture. You can also see how many servers and systems are impacted and to what extent and plan remediation accordingly.
Step 5: Report
After analyzing the issues, you must generate the results to create an effective strategy to fix those issues.
Nessus’s reporting capabilities include trending data and snapshots arranged intuitively. You can customize those reports to meet your needs by changing logos and titles instead of creating everything from scratch for each project. In addition, you can export the reports for client reporting and secondary analysis.
Step 6: Respond
Now that you have detected, evaluated, and analyzed issues and generated reports, you can respond to the problems highlighted. Although the process might seem lengthy, all this takes a lot less time than what it takes in manual ways. You can automate all these processes so you can take steps easily and resolve the issues to keep your systems and servers secure.
Who Uses Nessus?
Network Penetration Testers
Penetration testers can leverage the broad coverage and unparalleled accuracy of Nessus to run fully-fledged vulnerability scans to detect security issues before they can breach your security perimeter. They can use preconfigured policies and customize them based on their needs, use live results to detect the new problems, and generate reports to analyze and fix issues immediately.
Educators and Students

Educators utilize Nessus to teach students enrolled in cybersecurity courses. It helps them understand vulnerability assessment and management comprehensively.
Nessus is easy to use; hence, students can easily understand this complex and critical topic. This will help them identify vulnerability issues faster and fix them in time.
Security Admins
Security admins, especially from small and medium-sized organizations, can use Nessus to find security flaws, weaknesses, and underlying risks in their Linux and Windows servers and other systems. It can tell them the exact location of vulnerabilities so you can remove the vulnerabilities faster and save time.
Cybersecurity Consultants
Cybersecurity consultants help their clients understand the changing vulnerability and threat landscape to help prevent attacks and resolve them. They can use Nessus to find security weaknesses from their clients’ networks, servers, and systems and create a detailed report for them, summarizing their security posture. They can use this information to suggest remedies before any attack can happen.
Benefits of Using Nessus for Vulnerability Assessment
Businesses, including SMBs, should consider implementing vulnerability assessment solutions like Nessus in their security toolkit. There are many reasons that justify their need of considering this security strategy.
Let’s look at those reasons and understand how using such tools can benefit organizations.
Advanced Detection
Nessus has capabilities to cover a large range of vulnerabilities, around 65k CVEs (Common Vulnerabilities and Exposures). It is one of the highest in the industry. It can scan more software solutions, networks, servers, and other technologies to find a greater number of vulnerabilities. Thus, you will get a comprehensive view of every weakness and fight them.
Improved Security

Conducting vulnerability assessment with Tenable’s Nessus to find weaknesses and fix them helps you keep your servers and systems secure from the latest cyberattacks such as Zero-Day attacks, DDoS attacks, viruses, malware, and so on.
Tenable has researchers working on complex scenarios and leveraging extensive intelligence to help find more and more vulnerabilities and provide protection via plugins and other technologies.
Effortless to Use
Using Nessus is not at all challenging. It can be used by security teams, students, and professionals easily without hassles. It is created keeping in mind to simplify the security team’s complex and crucial tasks, with a motive not to complicate the process more.
All you need is a few clicks to create policies and scan your network, systems, and servers.
Easy to Deploy Everywhere
Deploying Nessus is easy as it supports various platforms such as Windows and Linux. This is a portable solution that is designed to be versatile and used everywhere.
Accuracy and Efficiency
Nessus’s technologies are advanced to provide accurate identification of vulnerabilities. It automates the process and makes it faster for you to save time. It is also efficient at highlighting all the security issues with their severity so that you can prioritize and address crucial ones first.
Cost-Effective
Conducting a vulnerability assessment with Nessus would not require you to spend a fortune. Whether you are a cybersecurity consultant or a team, you can use this solution at an affordable price. This is also why a lot of small and medium scale organizations love it since it offers quality and quantity while being cost-effective.
Power of Tenable to Scale
Nessus is operable across Tenable’s solutions. Hence, you can easily migrate to its platform – Tenable.io, and leverage additional insights for your IT ecosystem. In addition, you can combine different Tenable solutions and scale based on your vulnerability management requirements.
Pricing
Nessus is suitable for businesses of all types, specifically for SMBs. Don’t worry if you work in a team or as a lone warrior; it has pricing plans for every use case.
Nessus Essentials
This plan is ideal for students, educators, and individuals with a career in cybersecurity. You can download the solution for FREE and scan up to 16 IPs. It includes:
- High-speed, comprehensive assessments
- Support by Tenable Community
- Free guidance and training
- On-demand training
Nessus Professional
This plan is ideal for penetration testers, security practitioners, and consultants. It is available as a licensed subscription based on per scan. It costs
- $4,000.20 for 1 year,
- $7,800.39 for 2 years, and
- $11,400.57 for 3 years
It includes the following features:
- Unlimited scans
- Deploy anywhere
- Live results
- Configuration assessment
- Configurable reports
- Community support
- FREE 7-day trial
You can include add-ons such as advanced support 24×365 for $472 via email, phone, chat, and community. You can also add on-demand training for $230.10.
Alternatively, if you are looking for more capabilities for your growing business or enterprise-level organization, you can try Tenable.io – their cloud-based solution for vulnerability assessment and management.
Tenable.io
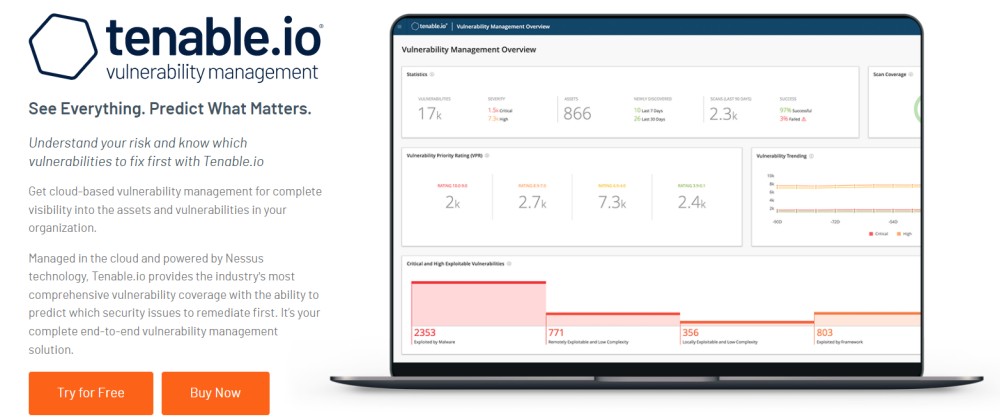
This vulnerability management solution is ideal for small, medium, and large organizations. It is licensed per asset. For up to 65 assets, it costs:
- $2,684.50 for 1 year,
- $5,369 for 2 years, and
- $8,053 for 3 years.
The prices increase with more assets. The features included in this plan are:
- Cloud-managed service
- Predictive prioritization
- Role-based access control (RBAC)
- Advanced reports and dashboards
- Enterprise scalability
- Advanced support via email, phone, chat, and community
- Instructor-led training courses
- FREE 30-day trial
Conclusion
Cybercrimes continue rising, causing damage to organizations of all sizes in terms of data, security, finances, and reputation. So, you must employ advanced solutions and strategies to encounter the attacks or at least minimize them. The first step of doing that is to safeguard your systems, servers, and all organizational assets via issue detection and remediation.
Hence, using vulnerability assessment solutions such as Nessus can help you identify weaknesses in your systems and Linux and Windows servers so that you can analyze and remediate them in time before they can cause harm. This way, regularly scanning for vulnerabilities will help you keep your systems and servers safe.
Si quiere puede hacernos una donación por el trabajo que hacemos, lo apreciaremos mucho.
Direcciones de Billetera:
- BTC: 14xsuQRtT3Abek4zgDWZxJXs9VRdwxyPUS
- USDT: TQmV9FyrcpeaZMro3M1yeEHnNjv7xKZDNe
- BNB: 0x2fdb9034507b6d505d351a6f59d877040d0edb0f
- DOGE: D5SZesmFQGYVkE5trYYLF8hNPBgXgYcmrx
También puede seguirnos en nuestras Redes sociales para mantenerse al tanto de los últimos post de la web:
- Telegram
Disclaimer: En Cryptoshitcompra.com no nos hacemos responsables de ninguna inversión de ningún visitante, nosotros simplemente damos información sobre Tokens, juegos NFT y criptomonedas, no recomendamos inversiones

