Phishing is a technique that criminals use to trick users into revealing login credentials, credit card details, and other private data.
Usually, attackers appear as if they are from known and trusted organizations. This enables them to trick the users into opening a compromised website link, malicious emails, attachments, or genuine messages.
A link could be a server that installs malware that steals sensitive information, such as login credentials and other private data, from the victim. Usually, attackers present malicious communication as if it comes from a trustworthy entity like a phone company or another service provider.
How Dangerous are Phishing Attacks?
A phishing attack is a big security risk, whether targeting an individual or an organization. Once they comprise a network, they can install malware, infect all the computers, and then use this to launch internal and external attacks. Additionally, the attackers may access sensitive company private data, which they could use to blackmail the organization or sell to competitors.
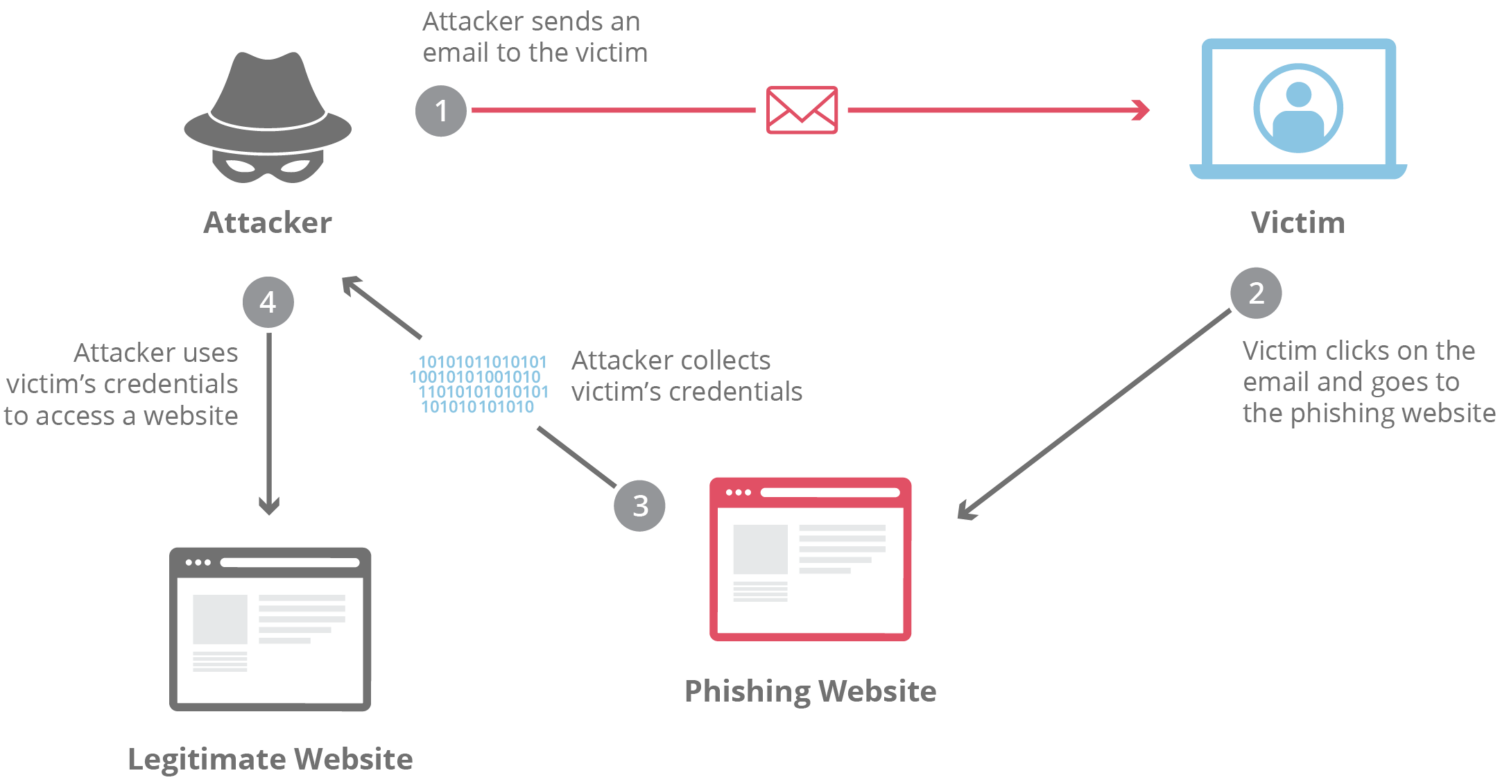
Once successful, the fraudsters often use stolen credentials, credit card details, or other private information to access other services on the victim’s network, make unauthorized purchases, and more.
Generally, a phishing attack may lead to reputation and financial losses for a company or individual. Also, the attackers could take the network down – leading to outages and huge financial losses. Another danger is losing the credibility and trust of customers, who may then move to a competitor.
Examples of Recent Phishing Attacks
Below are a few of the recent phishing attacks:
#1. Google and Facebook Fake Invoice Payments
Between 2013 and 2015, a Lithuanian scammer obtained over $100 million from Google and Facebook through a series of fake invoices masquerading from a large Asian-based manufacturer. Within two years, the fraudster sent several fake multi-million-dollar invoices resembling those from the supplier.
These included fake contracts and letters purportedly signed by Google and Facebook representatives. By the time they discovered the scam, the two had paid over $100 million.
#2. Colonial Pipeline Phishing Attack
A ransomware attack almost crippled the entire operations of the Colonial Pipeline in the USA. The 2021 attack compromised the billing systems and business network -forcing the company to stop most of its operations.
After getting an employee’s password through phishing, the attackers installed malicious ransomware software on the company’s network. This allowed them to compromise the systems and demand a ransom, which the company paid to avoid further damage and disruption of services.
Initially, the pipeline paid $4.4 million for the decryption key. However, the company lost more due to the one-week shutdown that led to the non-delivery of oil worth $2.86 billion.
#3. Sony Picture Spear Phishing Attack
In Sony Picture’s case, the attackers sent spear phishing emails to the employees after obtaining their information, such as names and titles, from LinkedIn.
Then, posing as colleagues, the attackers sent malicious email messages containing malware to the unsuspecting employees. The attack led to a breach that affected over 100TB of data, which cost the company over $100 million to sort out.
Types of Phishing Attacks
Bad actors use a variety of techniques to trick target users. The approach varies depending on the objective, and below are some common phishing types.
Spear Phishing
Spear phishing is an attack that targets a specific organization or person instead of random users. As such, it requires some knowledge of the target organization or user. The attacker must dig deeper and obtain inside information such as an individual’s power structure, personal life, hobbies, or anything they can use to customize the phishing message.
The attacker then customizes the message and sends it to the victim pretending to be a client, supplier, or boss requiring a change of invoice details or transfer of some money to a specified account. In most cases, recognizing a spear attack is difficult because the attackers trick a victim using accurate information about the user or organization.
Whaling Phishing
Whaling phishing is an attack similar to spear phishing but targets the company’s executives. These phishing emails, sometimes followed by a phone call, often lead to tricking the executives into authorizing payments to the fraudsters-controlled accounts.
Alternatively, the whaling phishers may trick the executives into revealing their logging credentials. Once successful, the perpetrators may perform a CEO fraud in which they use the compromised account of an executive to fraudulently authorize payment to their accounts.
Vishing
Vishing is a technique in which perpetrators use phones to scam unsuspecting users. The attackers pretend to be representatives from reputable organizations such as banks, telephone companies, etc.

During the call, they may trick you into providing sensitive information such as the mobile phone line pin. They could also request that you send some money to a specific account.
Some criminals may use a hybrid approach. In this case, they will first send a scam email and follow it with a telephone or vishing call, making it look more genuine.
Email Phishing
Email phishing is when a fraudster sends thousands of generic messages to different users, hoping that some will fall prey and make payments to the attacker. In most cases, they design phishing messages that mimic legitimate emails from a trusted company.

These messages will have the same templates, logos, signatures, phrasing, and other features that make them appear legitimate. Besides the messages, they create a domain that closely resembles that of a legitimate company, making it hard to suspect anything unless after scrutiny.
The fraudsters will also create a sense of urgency and threats, such as an account about to expire, unless the user takes action, such as resetting the password or paying some money.
Deceptive Phishing
Deceptive phishing involves perpetrators who impersonate a known and familiar email sender. Fraudsters often some legitimate links and contacts in malicious emails. As such, the email filters cannot block or flag the messages as spam.
Since the email looks genuine, the attacker may lead the user to reveal sensitive information such as banking information, login credentials, or some sensitive company data.
Criminals trick users by asking them to change passwords, verify an account, make payments, etc.
Clone Phishing Attacks
In clone phishing, the fraudsters create an email address similar to the legitimate one. They then email a user, who may share sensitive information with the criminals if not careful.
For example, an attacker may send a message that looks like it is coming from your boss and requesting you to share login credentials for a certain account. They might also masquerade as a vendor and request some payment details.
Angler Phishing
Angler phishing is an attack that targets users through cloned websites, fake private messages, or social media. In this phishing, the perpetrator looks for their target victims through social media. They then identify the people who complain a lot about a reputable bank, service provider, or other known organization.
The fraudster then masquerades as a customer support official from the organization and offers to help the complainer. At this point, the attacker tricks the victim into sharing login credentials or other sensitive data.
How to Identify Phishing Attempts
One of the effective methods of identifying spear and other phishing attempts is the SPEAR, as explained below.
- Spot the email or message sender
- Peruse the subject and ensure it is relevant to what you do and that it doesn’t sound off or unusual to what you usually receive
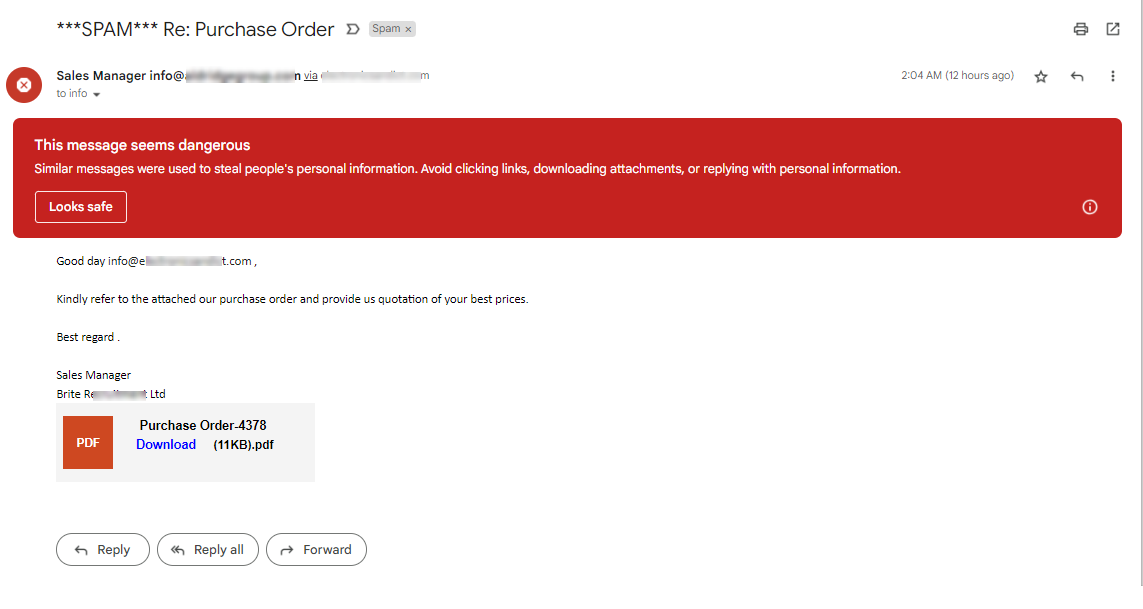
- Examine the attachments and links in the message. Hover over the links to see if they are relevant and matches the subject or requested action
- Assess the message to see if it is relevant and does not contain an unfamiliar tone, urgency, inconsistencies, grammar errors, or spelling mistakes
- Request confirmation from the genuine email account owner. Consider checking with the said sender if they have sent you that message.
Besides the above, here are additional tips.
- The email has inconsistent domain names, URLs, links, and email addresses
- A generic or unusual greeting, salutation, and language
- Email messages requesting personal or private data such as credit card details, payment information, login credentials, etc.
- An email message with a demand for urgent action, such as a requirement to change password, pay some money, and other actions
Now, let’s explore how we can prevent phishing attacks.
Preventing Phishing Attacks
Organizations and users can take various measures to prevent phishing attacks. Let’s have a look at it.
#1. Enforcing a Strict Password Management Policy
Admins could establish and enforce strong password management policies. In such cases, they should require strong passwords that users must change regularly. Additionally, users should not use a single password for multiple applications and should be prevented from reusing older passwords.
#2. Use Multi-Factor Authentication
Multifactor authentication ensures that a user passes several verification levels before accessing a service, such as a financial transaction. Even if an attacker obtains the credentials, such as a username and password, they will still require another form of authentication, such as providing a code sent to the genuine user’s registered device, such as a mobile phone.
Other multifactor methods include biometrics, badges, OTPs, Pins, and more. Since it is impossible for the attacker to pass the second authentication, even when they have the password, it is impossible to access and compromise the systems.
#3. Creating Employee Awareness
Conducting awareness campaigns for employees and the executive is one way of reducing the risks of phishing attacks. Its objective should be to promote safe online activities and empower the staff, including the executive, to identify and act on malicious emails.
Users should know the risks of clicking links or opening documents that look suspicious, as well as revealing sensitive information to strangers. Additionally, they should be discouraged from posting sensitive personal and company information on social media.
#4. Install Email Security Software and Tools
Install reliable and effective email security software to detect and stop phishing scams and other threats. Typical solutions include antivirus software, firewalls, spam filters, and more. Additionally, the organization can install web filters to detect malicious websites and prevent employees from accessing them.
#5. Not Clicking on the Link
Users should avoid clicking on links or attachments from unfamiliar senders. It is important to take precautions when acting on such emails, including those that appear to be from trustworthy sources.
In case it looks suspicious, verify the links by either hovering over them or copying them to a new browser window to see if it matches the content of the email.
#6. Ensuring Email Is From a Reliable Domain
Users should avoid opening or acting on emails from suspicious domains. For example, if someone sends you an email purporting to be from Microsoft, they are using an email address with a different domain. If in doubt, copy the domain name and search for it on the internet.
If its content does not correspond with the message, you should treat it suspiciously. Although most phishing emails are marked as SPAM, some may pass the spam filter and appear genuine.
#7. Avoid Giving Information on an Unsecured Site
If a link takes you to an unfamiliar site, you should not provide any sensitive or private information. You should never disclose your company’s or personal data to strangers; otherwise, the fraudsters may steal this information and perform unauthorized activities.
Final Words
Phishing attacks have been on the rise and do not seem to be slowing down as fraudsters continue adopting new tricks. While the organization can improve its security posture, risky user behavior is one of the major contributors to phishing attacks.
As such, using reliable security tools and safe online user behavior is one of the most effective ways of stopping attacks and ensuring the security and safety of your sensitive business data.
Next, you can check out the best URL scanners to check if a link is safe.
Si quiere puede hacernos una donación por el trabajo que hacemos, lo apreciaremos mucho.
Direcciones de Billetera:
- BTC: 14xsuQRtT3Abek4zgDWZxJXs9VRdwxyPUS
- USDT: TQmV9FyrcpeaZMro3M1yeEHnNjv7xKZDNe
- BNB: 0x2fdb9034507b6d505d351a6f59d877040d0edb0f
- DOGE: D5SZesmFQGYVkE5trYYLF8hNPBgXgYcmrx
También puede seguirnos en nuestras Redes sociales para mantenerse al tanto de los últimos post de la web:
- Telegram
Disclaimer: En Cryptoshitcompra.com no nos hacemos responsables de ninguna inversión de ningún visitante, nosotros simplemente damos información sobre Tokens, juegos NFT y criptomonedas, no recomendamos inversiones


